If you’ve run into that awkward moment in AWS when they ask you to submit your key into some suspicious-looking web interface in order to receive the password for your newly created instance, this quick command is for you.
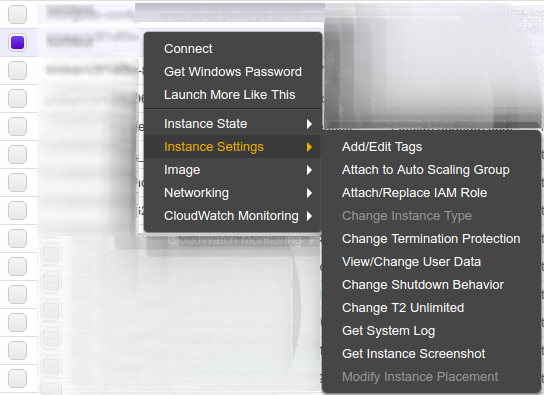
After an instance is created and running, right-click on the instance and select “Instance Settings” then “Get System Log”:
As you just booted your instance for the first time, the administrator password will be printed to the log:
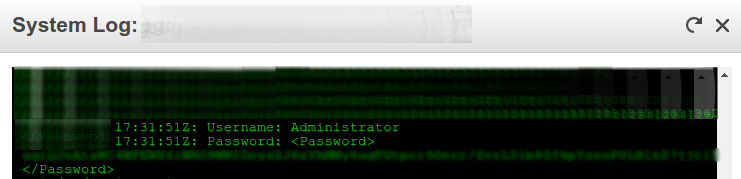
Copy the text between the password markup to your buffer and then paste it into this command along with the local directory of your pemfile:
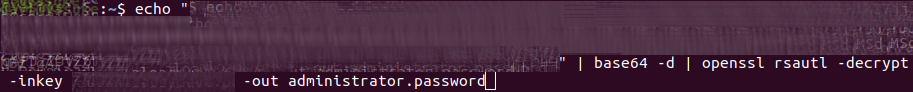
echo "copied-password" | base64 -d | openssl rsautl -decrypt -inkey "directory/pemfilename" -out administrator.password
Then open the administrator.password file and you’ll see the password for your administrator account
With EC2/SSH it’s possible to push out a new ssh key to allow access; ergo, if given access to the console, you can presumably add credentials as you wish.
So does this increase the threats in any way? It gives you another vector to obtain passwords. Probably an issue with multiple groups/users having access to the logs…