The other day I pointed out a strange disconnect between transit safety models in Holland and NYC.
While the Dutch claim their density is what causes their cycling safety, there’s no such effect in the US. San Francisco is far less dense than NYC yet far more progressive in terms of cycling safety.
Amazing analysis coming in from CityLab confirms the US has something else going on:
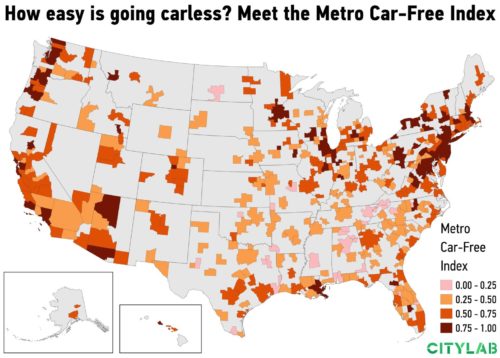
San Francisco tops the ranking of large metros in the index, followed by Boston and New York. What’s interesting is that the New York metro leads on three of the four variables of the index. It has far and away the largest share of households who report no access to a vehicle, 22 percent. (That’s more than three times the share in both San Francisco and Boston.) New York is also the clear leader in the share of commuters who use transit to get to work, with more than 30 percent, almost double San Francisco’s share. And it has the edge on the share of commuters who walk to work, roughly 6 percent.
But New York has a far smaller share of commuters who bike to work. It even fails to crack the top 10 on this metric, coming 101st out of 382 metros, or 22nd out of 53 large metros.
Full disclosure: I have commuted by bicycle in cities around the world all year through wind, rain, snow, sleet…up hills and down.
The reasons against cycling to work in NYC definitely are not topographical or weather related. San Francisco obviously is hilly and many other cities have comparable temperatures and precipitation than NYC.
56% of Copenhageners ride a bicycle for transport daily. 75% cycle all winter.

The core reason, I believe, is the politics of NYC and how they perceive personal power accumulation measured by dollar bills in their bank accounts to be inversely related to the health of the environment they commute in/through.
The city has a pollution-loving history with a huge “we’re busy trying to get rich/famous, leave us alone” lobby that claims doing the right thing for “others” is economically unfeasible in their list of priorities.
The term “economic feasibility” has been subject to debate in the past. When the city banned styrofoam, it said that recycling the stuff was not economically or environmentally feasible. Restaurants and other industry sued in disagreement — and it took several more years and some back-and-forth in the courtroom before the ban was finalized.
The typical NYC powerful resident would go to the gym and spin to look “better than others” in work or personal life, but has little interest in getting on a bike for the same workout when told it results in making the city a better place to live for others.
Anthropologists can probably explain why trains have escaped this dilemma, and it likely just has to do with momentum (Victorian cycling trends that benefited women most can be wiped off the streets in a day by car lobbyists, but it takes a lot more to kill popular yet unprofitable trains).
This of course is not saying NYC has no residents concerned with the environment.
It is to say the people who care have very little political power in a city filled with Napoleonic Ubermensches who blatantly ignore the genius lessons of Grant’s anti-Napoleonic ethic (memorialized yet disrespectfully hidden away at 122nd Street) and instead believe they must constantly be stepping on others to get ahead.
The city’s Five Borough Bike Tour shows how good-intentioned people of the city are so disenfranchised they have exactly the wrong attitude, marketing safe cycling as some kind of weird special event:
The idea of seeing all five boroughs in one day and seeing the streets shut down is such a unique opportunity
First, the streets aren’t shut down. They are being used more effectively. Stop calling proper use of streets to maximize throughput a shutdown.
Second, people are restricting their movements because cars make it so painful to go any distance let alone the magic 30 minute commute in a city that’s pushing a sad 40 minute average. Five boroughs is not actually much distance to cover in a day.
Third, this should not be seen as a unique experience. It needs to be a monthly event if not weekly. A single day for cycling to be made safe is pathetic in a city that claims it wants always to be “on” and alive.
I’ve written before about the benefits of cycling in cities and the bottom line is the economics are clear and simple. What’s unclear is who in NYC has the political power and sense to do the right thing?
The real story presented by Citylab data is bicyclists must find a LaGuardia-like talent to overcome NYC power culture now rooted in the self-gain mindset of cars that brings willful disregard for others’ safety and health.
Here’s what the National Motorist Association said to block NYC allowing multi-passenger high-density traffic priority over individuals in cars:
…what is really tedious is that we are not allowed to drive, but you expect money from motorists…
That’s crazy talk (absolutism and a fallacy), given how redirection from one street in an entire city doesn’t mean cars are being banned from all streets.
Think about what the motorist association is claiming: a single person who pays any amount of money demands that they are entitled to blockade hundreds or even thousands of others on the street just because they like to sit in public inside a private inconvenience box.

Drivers were being told they would have to avoid a street (small inconvenience) where a dedicated bus lane was being created for greater good… and that car association said no way would they allow smarter traffic planning if it takes away one inch of asphalt for them to generate harms, because they’re wealthy.
This is not an isolated case according to repeated psychological studies of motorists:
Psychologists Dacher Keltner and Paul Piff monitored intersections with four-way stop signs and found that people in expensive cars were four times more likely to cut in front of other drivers, compared to folks in more modest vehicles. …expensive cars drove right on by 46.2 percent of the time, even when they’d made eye contact with the pedestrians waiting to cross. Other studies by the same team showed that wealthier subjects were more likely to cheat…
If I were the city, I’d point out that motorists are heavily subsidized already and thus stealing from others by not paying nearly enough for the damage to infrastructure they cause:
American Infrastructure is crumbling. The ASCE has given American infrastructure a “D+”. It could cost almost $5 trillion to fully fix and upgrade American infrastructure. Congestion charging systems could potentially raise billions of dollars per year.
Here, let me frame (pun not intended) this another way: if a car is on the street then that street in NYC should be declared shut down.
I mean if we use that first point of the Five Borough Bike Tour properly, when cars use the streets the streets are effectively shut down and highly polluted (from brake dust to exhaust it’s a huge mess with slow cleanup).
People forget how influential and successful LaGuardia was dealing with the predatory and selfish mindset in NYC, and that his rural experiences and humanitarian values arguably are what made his vision of the city so great.
When will the next LaGuardia ride into town?