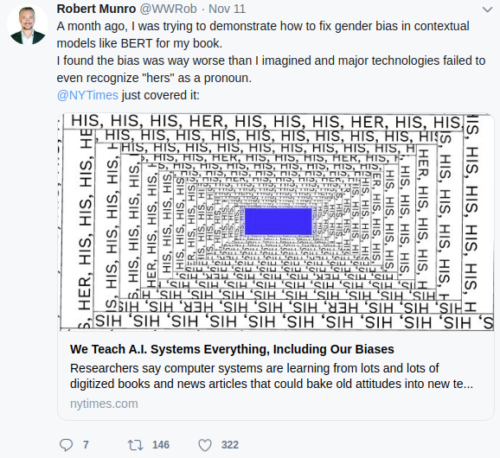
Leaflets have been so basic, so very black beret and prone to failures, that something higher up on the hat color chart seems to be in store for the military:
How better to attract talent into a modernizing Psychological Operations (PSYOP) group than a grey hat? Or imagine the “grey berets” calling in “knowledge bombs”…

Nothing is decided yet, I mean there’s still a chance someone could influence the decisions, but rumors have it that the next generation of psychological warfare troops could expect to be represented in a beret the color of white noise:
The idea is essentially still being floated at this point, but it could be a recruiting boon for the PSYOP career field, which is tasked with influencing the emotions and behaviors of people through products like leaflets, loudspeakers and, increasingly, social media.
“In a move to more closely link Army Special Operations Forces, the PSYOP Proponent at the U.S. Army John F. Kennedy Special Warfare Center and School is exploring the idea of a distinctive uniform item, like a grey beret, to those Soldiers who graduate the Psychological Operations Qualification Course,” Lt. Col. Loren Bymer, a USASOC spokesman, said in an emailed statement to Army Times.
While still being a little fuzzy on the details, reporters also dropped some useful suggestions in their story:
1) The new Army Special Operations Command strategy released just a month ago states everyone always will be trained in cyber warfare and weaponizing information
LOE 2 Readiness, OBJ 2.2 Preparation: Reality in readiness will be achieved using cyber and information warfare in all aspects of training.
2) Weaponizing information means returning to principles of influence operations in World War II (e.g. Mission 101, and Operation Torch), let alone World War I (e.g. Battle of Beersheba)… I mean adapting to the modern cloud platform (Cambridge Analytica) war.
The Army Times article also states:
“We need to move beyond our 20th century approach to messaging and start looking at influence as an integral aspect of modern irregular warfare,” Andrew Knaggs, the Pentagon’s deputy assistant secretary of defense for special operations and combating terrorism, said at a defense industry symposium in February. Army Special Operations Command appears to take seriously the role that influencing plays in great power competition.
Speaking of cloudy information and influence, an Army site describes how the Air Force in 2008 setup a data analysis function and referred to them as Grey Berets, or Special Operations Weather Team (SOWT):
As some of the most highly trained military personnel, the “grey beret” are a force to be reckoned with. Until SOWT gives the “all-clear” the mission doesn’t move forward.
The Air Force even offers hi-res photos of a grey beret as proof they are real.

Meanwhile over at the Navy and Marines there’s much discussion about vulnerability to broad-based information attacks across their entire supply chain.
…a massive cyber campaign is being waged against the Navy, and every organization associated with it is mounting. The defense industrial base and associated supply chains are under constant assault. The hackers have two objectives: steal U.S. defense secrets and undermine confidence…
This might be a good time to remember the day of October 12, 1961 (only nine months after taking office as the President), when JFK visited Fort Bragg’s Special Warfare Center.
While Brigadier General (BG) William P. Yarborough, commander of the U.S. Army Special Warfare Center, waited at the pond, the presidential caravan drove down roads flanked on both sides by saluting SF soldiers, standing proudly in fatigues and wearing green berets.

General Yarborough very strategically wore the green beret as he greeted JFK and they spoke of Special Forces wanting them a long time (arguably since 1953 when ex-OSS Major Brucker started the idea).
A few days after the visit in October 1961 JFK famously wrote poetically to the General:
The challenge of this old but new form of operations is a real one…I am sure the Green Beret will be a mark of distinction in the trying times ahead.
Just one month later, 58 years ago (November 1961) the green beret became official headgear of the Special Forces, which earlier that year started being deployed into Vietnam. Finally on April 11, 1962 JFK issued a White House Memorandum to the US Army:
The Green Beret is again becoming a symbol of excellence, a badge of courage, a mark of distinction in the fight for freedom.
What will the grey hat symbolize and what will become its history?
Update May 2020: Perspective from USSOCOM on SOF and US Strategy.
“During his most recent trip to Afghanistan, Clarke said, he found that commanders now spend 60 percent of their time working in the information space. Commanders think about how to use the information space to influence the Taliban’s thought processes and how to influence the Afghan.”
Update July 2020: ArmyTimes wrote up “How the Green Berets got their name”
Founded in 1952 as part of the U.S. Army Psychological Warfare Division, the 10th Special Forces Group was the first of its kind, according to Army archives. It was named the tenth group to make the Soviets think there were at least nine others just like it, Anne Jacobsen wrote in her book “Surprise, Kill, Vanish.” […] Wanting to distinguish themselves from conventional Army forces, Special Forces soldiers selected the wear of the beret because of OSS influence, since a number of its teams adopted headgear worn by soldiers in France. And the color green came from the influence of British Commandos during World War II.
Update April 2021: SandBoxx writes…
U.S. Special Operations Command (SOCOM) has created a new joint task force to fight against Chinese information operations in the Pacific.