Too often the news focuses on the attacks that succeed and not enough on those that fail. We should balance. There are several lessons to be learned from the most recent al Shabab suicide bomb attacks that failed in Somalia.
Let me back up a step first. This isn’t exactly history, but I find it hard to believe half a decade has passed since I was warning about social fitness networks in the cloud, such as Strava.
They immediately seemed to me a dangerous surveillance system with serious confidentiality risks.
strava posts surveillance of runners and bikers https://t.co/CbA3wzVQ5k
— davi (((🐧))) 德海 (@daviottenheimer) May 4, 2014
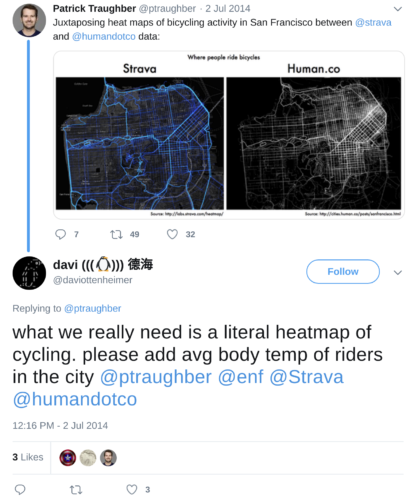
To be fair, given closed networks with data ownership and the person generating given reasonable boundaries, I also made a point how heatmaps could be safely used like any performance monitoring tools.
ITV heatmap of Ronaldo movements shows his limited effect https://t.co/gpblQlgcJP pic.twitter.com/Hp8Oxbk2Qb #USAvPOR
— davi (((🐧))) 德海 (@daviottenheimer) June 22, 2014
However, we’ve been talking about the realities of securing big data for nearly a decade here, which tends to mean at public services scale where confidentiality is not well protected let alone understood.
On that level I was warning directly about cloud services being in a position to destroy privacy for thirsty valuation-focused executives who were giving little to no thought about the consequences to the entire information market when trust collapses.
Please excuse the snark here, but my point was we fast were approaching total information awareness. I was giving a lot of talks about the risks at this point with maps like these:
All of this is background to the fact that Strava was instrumental in leaking Joint Special Operations Command (JSOC) presence. JSOC likely was unintentionally giving away their secrets so that Strava could generate heatmaps of people jogging around a military airfield in Baledogle, Somalia used for drones (also by 2015 it was disclosed by FP).
Somali government and AMISOM sources confirmed the existence of a second clandestine American cell in Baledogle, the site of an abandoned Cold War-era Air Force base in Somalia’s sun-blasted Lower Shabelle region. These sources estimated that between 30 and 40 U.S. personnel are stationed there, also carrying out counterterrorism operations that include operating drones.
Unlike parsing heart rate and body temp to pinpoint someone in San Francisco, however, Americans running in Somalia kind of stood out the minute their Strava data uploaded.
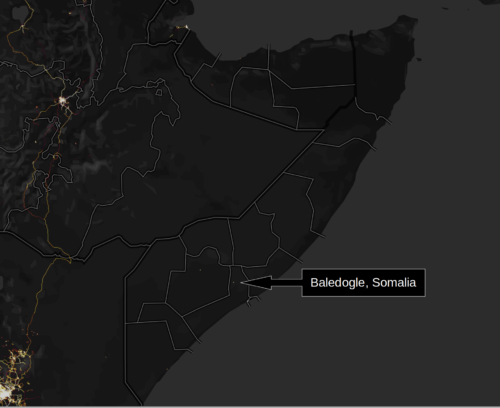
See what I mean?
Again to be fair, I was doing some of this publicly in 2014 to other countries as well:
this is fun. finding a lot more geotags for tweets in north korea than cars on the road pic.twitter.com/24h9mEzW8v
— davi (((🐧))) 德海 (@daviottenheimer) December 31, 2014
Why is this so significant in today’s news? Reuters is quoting sources who give credit to failed suicide attack planners for having good intelligence about American movements on that base.
The attack showed al Shabaab maintains a good intelligence network and can mount complex operations, said Hussein Sheikh-Ali, a former national security adviser and founder of the Mogadishu-based security think-tank the Hiraal Institute.
The attack hit a part of the base that houses U.S. special forces, who supervise Somali forces on operations, he said.
“It implies they have a high intelligence and a degree of capability just to get close to that place,” he told Reuters.
I’m not going to argue against the source, just qualify that good intelligence network might in fact mean someone has a browser and Internet connection to monitor US soldier Strava data that is not being protected by the service provider or that service provider’s service providers.
The point remains that the attack failed completely. Not only did the dual suicide bombers cause zero casualties — blowing up selves at outer perimeter defense system — their entire terror team of 10 was killed.
Somali state news agency SONNA reported that all the militants who took part in the assault had been killed.
“In response to this attack and in self-defense, U.S. Africa Command conducted two airstrikes and used small arms fire targeting al Shabaab terrorists,” a U.S. military statement said.
Some secrets still are safe for that perimeter to have worked.
Interesting also is the qualification of self-defense in this event. It suggests the attackers were pursued outside the defense perimeter to be engaged and eliminated. That’s not yet been reported, it’s just a guess based on the qualified statement.
If you think my warnings in 2014 were accurate, even foreshadowing, I mention the defense perimeter angle here because of its relationship with recent domestic “hunt” legislation that in a very remote sense (pun not intended) could be abused to authorize drone strikes as self-defense almost anywhere.