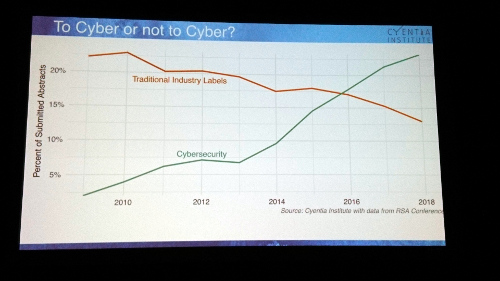
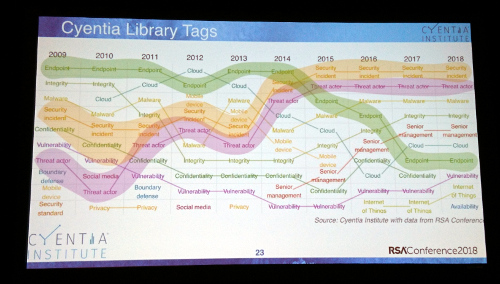
Keynotes on 30 second delay stream to public
RSA Announcements
Women in tech
Message of diversity
Microsoft Announcements
Call for a digital Geneva convention (https://twitter.com/BradSmi/status/831553031422386176)
– No targeting
– Assist private sector
– Limit offensive ops
– Restrict cyber weapons
– Non-proliferation
– Report vulns
Shipping a secure linux kernel because “Microsoft now is a Linux company”
Tech Sector Accord
– protect all users and customers everywhere
– oppose all cyberattacks on innocent citizens and enterprises
– provide tools and info to help community protect self
– deepen co-operation & information sharing between companies
Five-eyes are collaborating on blaming attack on North Korea
Message of unity: “It about trust…we need the world to come together”
Message of diversity. Bring different kinds of people together: “learn, change and grow” to “build a safer world”
Award Stuxnet: Michael Assante
Award Public Policy: Admiral Michael Rogers
Award Math: Ran Canetti, Rafail Ostrovsky
Award Humanitarian (created by yours truly): Tim Jenkin
McAfee
An ode to the Skyjacking Threatscape security evolution
1961 became a crime after Cuban revolution
1972 peak of hijacking, nuclear threat
1973 passenger and bag screening
2001 post-sept slow and long lines
2006 3-1-1
2009 underwear scans
User the airline model: “if you look to the air travel industry, obsessive about safety and security”
“Think about what you can take back from this to our offices…try to drive a culture where security gets prioritization it deserves.”
Cryptographer Panel
Moxie
Paul
Whit
Adi
Ron
Interesting year
Ron
– elections interest. central to democracy. crit infra.
– spectre attack
Adi
– lack of preciseness in research. crypto has theorem/proofs. no cyber equivalent. need quantitative
Whit
– memory of wife, elder of cryptography, partner enthusiasm. everyone loved mary. marty’s fondness
– mayland doyle. most influential cryptographer at RSA (sig sally pivotal to development of cryptography). worked on KI-1. designed crypto for KY-3 used for 30 years. KG-30 designed, long-cycle decrypters.
paul
– performance security tradeoffs. security gains have equalized with performance
moxie
– shift in perception of technology. connecting the world no longer utopian. cyber now seen as weapons not connecting
Bitcoin
Adi
– pronounce differently
Whit
– spell differently
Ron
– hashing for crypto far greater than for security
Whit
– space heaters based on crypto, amortized cost of hashing
Blockchains
Ron
– not pixie dust. interesting decentralized, public, immutable. fail at scale, throughput and latency
– really bad for voting because centralized and secretive. electronic database doesn’t allow verification by voters. paper is better choice
Adi
– overhyped. post-quantum world ensure security of digital signatures. 50 years valid guarantee of digital signatures. generated today before quantum computers available. doesn’t matter if new tech comes, show early generation of signature
Whit
– when you don’t have to have secrets you shouldn’t
Paul
– commercial applications
Moxie
– distributed nature is valuable, not many applications of that in real world. consumers see as zero value. distributed systems tend not to work. like P2P craze of 2000s
Quantum compute
Adi
– Microsoft talk, prediction of his boss. first qbit by end of year. computer in five years. distanced self from prediction.
– 82 proposals, 64 remain. three main groups. 26 proposals based on lattice. 19 based on coding theory. 9 based on multivariate. 3 based on hash-based. all schemes had to be nailed-down, fully specified. surprised by speed. most few milliseconds. some hundreds of microseconds. key sizes 1 and 10 kbytes.
Ron
– how many came from proofs?
Adi
– proofs were fairly weak. NIST will have hard time within three years professing a winner. took 15 years for RSA to be accepted. took 15 years for eliptic (1985 to 2000s). hard to design and tricky. fortunately one suggestion time-tested. post-quantum RSA
Whit and Adi get into a fight
Paul
– don’t omit looking for hash-based solutions for digital signatures
Adi
– NIST will choose one of the hash-based because evaluated a long time
– only incremental progress on computers, long away from something that will break crypto
Adi
– would accept improvement in any area. instead, silence
System level bypass
Paul
– found old presentation and noticed the exploit. noticed google had done same. found twice within a few months.
– who can fix hardware in process, who can notify? press leaks ended up in panic end to embargo. decision was made to release early. failed twice with embargo. need ethicists to create a roadmap
Adi
– worried we get to point massive amount of processors would be bricked. huge disaster
Paul
– we have a huge mess. guidance is instructions on all your paths. slow and tools don’t exist. lots of work to be done.
– in context lots of bugs. hardware bug doesn’t change aggregate issues
Ron
– hard to avoid leakage on shared systems
Paul
– we have to start bifurcating and dedicating hardware
– build systems with primary security objective
Apple iCloud hosting in China, with keys there
Adi
– not exceptional when everyone has access
Paul
– China in for surprise when their data gets hacked. won’t end well
Ron
– EU commission report in favor of strong encryption. back doors bad for security, as well as privacy
Moxie
– it’s easier to say i can’t instead of i won’t. hard to resist
Broader implications beyond China
Ron
– FBI wants access, but they didn’t try very hard to get into SB phones
Paul
– idea that you suck up all the data to make sense of it. these kinds of processes create risk by putting tools/data in one place. corporate level trade-offs easy to see. nation-wide scary
Adi
– telegram told give keys to russia. refused. telegram became illegal. banning schemes they don’t have master key for
Moxie
– easier to say i can’t than i won’t. if design without key, then can’t give
Paul
– wasn’t in their interest to protect our data. risks we incur are not us. facebook made decision to hurt users. didn’t build system to protect users. companies that benefit won’t help
Whit
– economics. more money means weaker processors. same for databases
Paul
– Bain conclusions on cost to society
Moxie
– Facebook is the Exxon of our time. indispensable tool everyone despises. as much as everyone hates Exxon, dumps oil in ocean. Exxon is civilization and Facebook is the Internet. Facebook going through Exxon moment and people thinking better tech investment time
Adi
– EU fines for GDPR huge (4%). plan B of EU to tax american companies (couldn’t get it one way, so get it other way).
– interesting issues there. look into it because can impact
Moxie
– GDPR can entrench monopoly. good for them because refuse service if don’t consent, but they’re the internet
Adi
– goes beyond. privacy by design, default, mandatory encryption, right to erasure
Silver Linings in Cloud of Security
Ron
– we’re in era we feel attackers are winning. where are they focusing, what will we defend. 2/3 people on paper ballots. voting the hard way is the silver lining
Adi
– moving at high velocity. didn’t mention forward or backward. silver lining is our job security guaranteed
Whit
– don’t have to find new job
Paul
– band on the titanic is small silver lining. complexity growth will lose us the battle. better hardware is optimistic. more things than just crypto being robust. make a chip of low-chance of buggy
Moxie
– privacy and crypto tech less about shards of info, more like infrastructure for the world we want