While writing this week about the Russian “Vulkangruppe” attacking Berlin, I was reminded of the Sony hack attribution games we played a decade ago.
The isolationist narrative of DPRK was always wrong. It served people who wanted easy answers in both directions. The harder truth has been that North Korea leaked evidence of its Russian-enabled connectivity for nearly twenty years, as anyone willing to trace the rails and cables would know.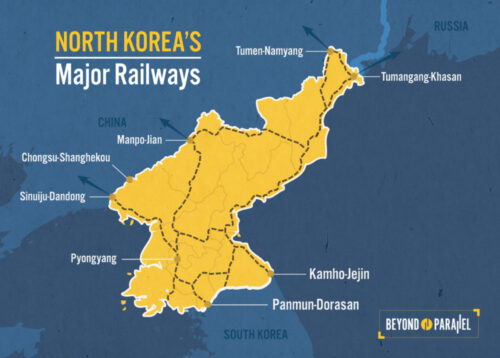
I don’t take victory laps on attribution. But I’ll take one on the flyingpenguin blog methodology, because it might help set context for what’s happening in Germany today.
In January 2015, I published an investigation here that traced North Korea’s internet infrastructure to Russia.
Remember?
The security community was so busy arguing about whether DPRK was sophisticated enough to have hacked Sony, I doubt anyone noticed the more mundane proofs right in front of them. When the usual skeptics insisted the hermit kingdom lacked connectivity, while the FBI asked us to trust classified evidence, both seemed unnecessarily closed minded.
I took a different, rather classic, approach: follow the open rails, look for the exposed cables.
This is how I identified Russian TransTeleCom as the likely provider, which led to identification of even far greater Russian involvement. I traced their fiber network to the border, by following the railway. I found the Khasan-Tumangang crossing and located photographs showing cables running across the bridge into North Korea. And I noted this was a decade after the 2006 agreement between TTK and the DPRK Ministry of Communications.
In September 2017, 38 North and FireEye finally confirmed that TransTeleCom had gone live as North Korea’s second internet provider, using exactly the infrastructure I’d documented on this blog two and a half years earlier.
The connection runs through the Friendship Bridge at Khasan-Tumangang, precisely where I’d spotted the cables on a pole.
Fast forward to today and Trend Micro published research in 2025 on North Korean cyber operations, officially identifying Russian IP ranges in Khasan and Khabarovsk as key infrastructure for DPRK offensive activity. They note the railway station at Khasan facilitates operations across that exact same bridge I was showing photographs from Panoramio a decade ago.
…North Korea’s significant role in cybercrime – including campaigns attributed to Void Dokkaebi – is facilitated by extensive use of anonymization networks and the use of Russian IP ranges. …Ukraine, US, and Germany have been targeted in these campaigns…
The methodology holds. PR maps, rail schedules, flight routes, treaty boundaries, and even eye-level photography. None of it means classified access or insider sources. It is only following physical infrastructure through physical territory to find the copper or glass running through places controlled by states with interests.
The same methodology applies today when we are tracing who’s really attacking critical infrastructure. Find and follow the burned cables in Berlin or San Francisco, and watch how you end up looking at a heat source from Russia. Protip: look wherever AfD shows interest.