This idea came up the other day as a follow-up to the XKCD strip…and it just seemed like the kind of thing that would look good on a billboard. I guess I could have left it “i’m loving it”, as in IT, and made it “sudo makemeasammich” but I couldn’t resist the irony of celebrating root(s) at a fast food company.
Monthly Archives: July 2011
National Cloud BBQ on a Train Nightmare
A TechTarget writer has written an emotional rant against regulation of cloud computing. It’s thick with prose and allegory, perhaps to hide the fact that it has little to offer the reader in terms of logic and reason. Here’s a fine example:
The cloud train is rolling, and locomotives (and their engineers) do not appreciate it when morons in suits barge in and start pulling levers for no earthly good reason. I’m all for consumer privacy and commercial accountability; pass laws that simply forbid bad actions, not make technologists and enterprises jump through crazy hoops.
Simply forbid bad actions? What makes it so simple? No explanation of these simple laws is offered and they seem to contradict with his earlier argument.
First, he is asking for a blacklist, or a list of things that are disallowed. A whitelist would be a list of things allowed. There are flaws in both lists (and blacklists are especially hard to write well) so it’s best to have a balance of each.
Driving a car, for example, you will see signs that say “No right turn” as well as signs that say “Speed 55”. A car that makes a right turn is violating the blacklist, a car that drives more than 55 is violating the whitelist. Actually, to be more accurate, anyone who is driving a speed that is “safe and prudent for current conditions” is on the whitelist. Imagine an intersection that has a sign posted for every conceivable “bad action” with a vehicle and you will see why blacklists are not so simple.
Second, let’s say we go along with the author’s suggestion and only write blacklists, we still need cloud environments to accept them. The common way to audit a company for adoption of a rule is to review their written/documented policies. So it’s probably safe to say that the author intends for his “forbid bad actions” laws to be turned into company policy, which then needs to be audited. That turns out to be what is being proposed and yet what he is trying to complain about — a contradiction.
The DATA legislation, for example, would call for IT shops to “require each person engaged in interstate commerce that owns or possesses data containing personal information, or contracts to have any third-party entity maintain such data for such person, to establish and implement policies and procedures regarding information security practices for the treatment and protection of personal information.”
No matter where you or your data resides, it is subject to audits on demand. Your data management tools can handle that in a snap, right? On no wait, they can’t. Those tools don’t exist. Looks like you’ll be on your knees begging sales, HR, your payment processors, your vendors, your partners and your customers for all that crap — and legal will still find a way to blame IT.
His interpretation is clearly off the mark (another reason why blacklists are not simple). The legislation he quotes asks an auditor to confirm that polices and procedures for security practices are in place. This is not a request for “data management tools”. Note the contempt the author has for “legal”. Perhaps it’s the same contempt he has for the “morons in suits”?
The author is basically expressing frustration with regulation at a very visceral but unqualified level. We’ve all been there. Then we calm down and do the research. Some laws are just written poorly and need to be improved, while some laws are based on real harm. Thus, without quantifying a negative example, his argument boils away entirely. The one and only case he gives us is that some people” he knows use multiple systems.
“The move to the cloud is one of the defining information technology trends of the early 21st century,” says John Villasenor of the Brookings Institution. Therefore, he writes in part, the feds should probably clarify what it means to read regulated email or electronic documents on your phone while overseas.
Please, dear god, no. Do not do that. I’ve seen federal data standards in action. I know people with two phones and three computers they have to use for different federal requirements. They have to fill out paperwork if they send an email from the wrong device. It’s like Kafka meets Cthulhu and the end result torments your soul in non-Euclidean email shape for the rest of eternity.
I’m missing the jump from using three different devices to Kafka and HP Lovecraft. And then to prayer? Seriously. I use dozens of devices for different requirements every day and if I make a mistake that involves risk to others’ data, then I’ll be filling out paperwork. It makes sense to me when regulations reflect appropriate ways to deal with risk. I see the 50% risk reduction from seatbelts and I take the time to put mine on, even without the fine.
Incidentally, religion and god…very regulatory.
I could tell all my clients to just trust me and keep their audits and regulations to themselves, but that’s not going to compete very well when there are others who agree to the common practices of transparency and disclosure in their work. In other words, and to turn it around, those who want to compete on a level playing field will appreciate rules that embody common practices to reduce risk. Restaurants who keep their kitchens clean to protect the health of their customers also do not want to be disadvantaged against their competition for doing the right thing (whitelist).
As much as I would like to say that I find the author’s playfulness with language amusing, instead I find his style has too much emphasis on apathy and impatience. Compliance is “extremely boring”?
Two items in the extremely boring but very important arena of federal regulations came up this week that touch on cloud computing…
[…]
If you think that reporting on, reading about or examining federal regulation of the IT sector is hot stuff and not boring, I do not want to come to your cookout. However, it is incredibly important right now, in the same way a truck is incredibly important when you are standing on the highway.
Oh no, risk mitigation is coming. Hide the kids before the risk reduction measures are here. The truck simile makes no sense.
I’m sure he would turn down my invitation to a cookout, since I would have put it the other way. If you think everything and everyone should get out of the way of a truck just because it’s barreling down the highway…then you either don’t believe in the market for brakes and suspension products or you under appreciate how exciting it can be to help save lives and create prosperity. The nightmare is a world that has no way to stop giant trucks from running us over.
Guerrilla Greywater: Living Off the Grid
Tips from KALW news on some do-it-yourself waste management.
The process is pretty simple: the poo bucket is under the house. It gets emptied once a week into a larger rain barrel. Once it’s full, Laura covers it and lets nature take over. And in one year, voila! You have humanure.
And you might be wondering – what about the smell? Well, the sawdust, coupled with an air vent, creates an anaerobic process: it doesn’t smell. Laura’s bathroom actually smells clean, with a hint of cedar wood, thanks to the sawdust. And the urine? Laura collects that too, in a separate container which she uses as a fertilizer for her garden. Human urine is rich with nitrogen, which plants need to grow. She almost gets more excited about urine diversion than composting.
[…]
In Laura’s bathroom, there’s a large photo of a few ears of corn. Some were fertilized with urine harvested from her toilet; some were not.
ALLEN: You can see in the picture that the zero-urine corn is tiny – like two inches tall. And the cobs that received the most urine are big, yellow, and, like, eight to 10 inches long. So it’s very visual, how well it works.
Note: the group no longer calls itself a Guerrilla group to avoid association with other meanings of the word. I guess they decided it would be too hard to reclaim the word and strengthen the non-violent associations.
In 1999 we named ourselves the “Guerrilla Greywater Girls” as a tongue-in-cheek response to a draconian California plumbing code that discouraged the simple, low-tech greywater systems we promote. A few years later we changed our name to the “Greywater Guerrillas”, to reflect the multi-gendered composition of our collaborators. As we worked more closely with government agencies and regulators, and began collaborating with A Single Drop in countries where “guerrillas†has violent implications, we searched for a name that would represent our goals and strategies to a diverse and international audience. In 2009, we chose a new name— Greywater Action- For a Sustainable Water Culture—for our appropriate technology education projects. We’re also developing an umbrella group that connects the art, appropriate technologies, theater and cultural transformation around water.
Pwning the 2004 Presidential Vote in Ohio
A detailed review of serious security weaknesses in the 2004 Ohio presidential election system has been posted in the Free Press by co-council on the case.
The system appears to have been under-built and then, as the final tally was run, it switched processing over to an unmonitored and insecure location in a different state operated by a company with a close association to the winning candidate.
The King Lincoln Bronzeville v. Blackwell briefs are cited:
The filing also includes the revealing deposition of the late Michael Connell. Connell served as the IT guru for the Bush family and Karl Rove. Connell ran the private IT firm GovTech that created the controversial system that transferred Ohio’s vote count late on election night 2004 to a partisan Republican server site in Chattanooga, Tennessee owned by SmarTech. That is when the vote shift happened, not predicted by the exit polls, that led to Bush’s unexpected victory.
SmarTech, the location of the servers in Tennessee, is perhaps most infamous for hosting Republican Internet domains — not the sort of environment one would expect to be used for a voting system. It was also later the site used by the Bush White House staff “to evade freedom of information laws by sending emails outside of official White House channels”.
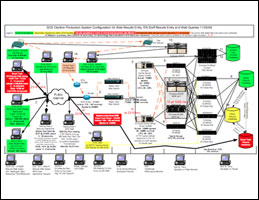
The location and partisanship aside, I find it extremely hard to believe there is not a single firewall let alone a DMZ architecture in the network diagrams. It must be a mistake. Were the vote databases really setup on a flat network?
These details of the network have been revealed only after a fight with Connell, who argued that they should be kept a secret while public — yes, it’s a contradiction.
Connell is refusing to testify or to produce documents relating to the system used in the 2004 and 2006 elections, lawyers say. His motion to quash the subpoena asserts that the request for documents is burdensome because the information sought should be “readily ascertainable through public records request”; but also, paradoxically, because “it seeks confidential, trade secrets, and/or proprietary information” that “have independent economic value” and “are not known to the public, or even to non-designated personnel within or working for Mr. Connell’s business.”
It’s not the first time I have heard this odd and duplicitous argument from a network engineer. A District Attorney (DA) recently said he sent a man to jail for a similar argument in a fight with management. The engineer argued that the government network he was working on was copyrighted (public record) but secret.
The parallels continue. This other man, now in jail, had built a Man in the Middle (MitM) architecture. Connell is accused of creating the exact same security flaw. The Free Press cites “IT security expert Stephen Spoonamore”, who gave a sworn affidavit to the court, that the Ohio presidential network design was intentionally designed to allow a MitM attack.
Until now, the architectural maps and contracts from the Ohio 2004 election were never made public, which may indicate that the entire system was designed for fraud. In a previous sworn affidavit to the court, Spoonamore declared: “The SmarTech system was set up precisely as a King Pin computer used in criminal acts against banking or credit card processes and had the needed level of access to both county tabulators and Secretary of State computers to allow whoever was running SmarTech computers to decide the output of the county tabulators under its control.”
Spoonamore also swore that “…the architecture further confirms how this election was stolen. The computer system and SmarTech had the correct placement, connectivity, and computer experts necessary to change the election in any manner desired by the controllers of the SmarTech computers.”
Given the DA explanation of the other case it is possible the outcome of this one might go the same way. It’s a great example of the reality of insider and domestic threats. While much of the news talks about the foreign threats to US government infrastructure, it is always worth considering that weaknesses in networks may be intentionally created by insiders who seek an unfair advantage.