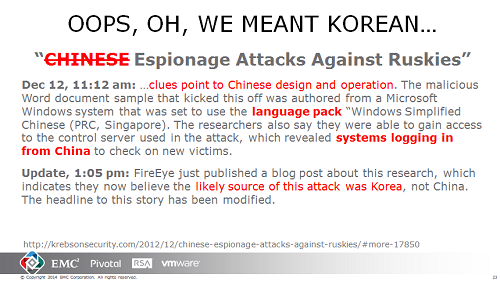
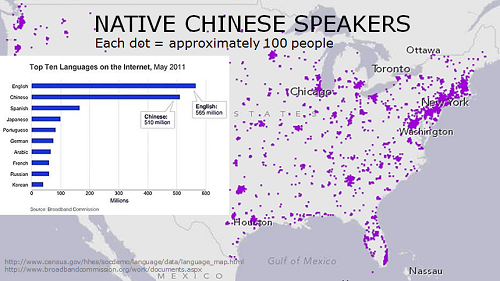
The Microsoft take-down of malicious DNS has stirred a healthy debate. This is the sort of active defense dilemma we have been presenting on for years, trying to gather people to discuss. Now it seems to be of interest thanks to a court order authorizing a defense attempt against malware: take-over and scrubbing of name resolution.
Over the past several days I have been in lengthy discussions with numerous lawyers on mailing lists about legal and technical details to the complaint and action. Some have asked me to put my thoughts into a blog, so here you have it.
This dialogue with both lawyers and security experts has crystallized for me that a community trying to increase freedom on the Internet should be, and some already are, supportive of elements in Microsoft’s action.
There is an opportunity here for guiding courts to course-correct and increase the effectiveness of individuals or even groups using active defense to reduce harm with minimal impact to freedoms. One exception in the security community stands out; some said the organization implicated in harm was sufficiently responsive before Microsoft action and should have been left alone to continue dispensing at current rates. Hold that thought.
Throughout my entire career, just to put this in some perspective, I have been an outspoken critic of Microsoft. My site name, flyingpenguin, started in the mid-1990s as homage to Linux and in belief that it would ultimately bypass Microsoft. This was in part due to coming from a VMS and Unix background and then being asked in my first professional job to lock-down and defend Windows NT 3.51 from compromise. It was hairy bad.
Anyone remember Bill Gates saying NT would ship but security can wait? Or remember Microsoft’s founder telling the UNIX community they have to explain to him how to make a billion dollars with security? My 2011 Dr. Stuxlove presentation started with some of those stories.
Ok, a full confession: I was offered PCs with Microsoft Word at home but I preferred WordPerfect and switched to Apple as soon as I could (1990, although I stopped using Apple in 2010). Despite preferences, I also accepted my fate as a security professional, which has meant 20 years spent working on ways to protect Microsoft customers.
To me, for as long as I can remember, Microsoft really seemed like a law firm started with lawyerish intentions; it just happened to also write and sell software. I might have further hardened these views due to years I spent watching legal trickery used like cannons to sink all the competing software boats; obvious hostility and attempts to knock holes into hobbyist and free software movements.
That legally-led-and-defended direction against competition didn’t last forever for various reasons outside the scope of this post. But Microsoft gradually was forced by external factors to realign their definition of malice away from competitors and hobbyists and towards clearly malicious software as well as some glaring flaws in their accountability department. The change started around 2000. By 2005 I was invited inside for a meeting where I was told “we now have five people full-time on security”. Five, in the entire company; don’t know if that was accurate but apparently 1/5 of the Microsoft security group saw me almost fall out of my chair.
Today, despite the thick jade-colored glasses you might think I wear when looking at Microsoft, I can see a different company taking very different approaches to security. Microsoft is *cough*, I can’t believe I have to say this, emerging as a leader and committed to improving safety in some balanced and thoughtful ways.
I was surprised to be invited to another internal meeting in 2013 but was even more surprised to see how thoroughly a security message is working its way through the organization. Don’t count me a full supporter yet, however. I’m still a skeptic, but I have to admit some noticeable changes happening that I wanted to see. Either they’re really getting it or my bullshit detector is failing. Of course both are possible but I believe it is the former.
Microsoft in the past few months appears to have rotated their massive legal cannons to fire volleys of legal briefs upon those they find willingly causing catastrophic harm to Microsoft-made vessels. Am I using the “letter of marque” analogy too liberally here? Microsoft is asking the legal authority for permission to fire, opening their plans for assessment by that authority, and claiming they will act responsibly within limits defined by the authority. We might actually want this to happen more. After all, if Microsoft does not try to actively help in the defense of their users from harm, who should we turn to and ask for a better job with less risk?
Let me try with another analogy. This one might resonate closer to home (pun not intended). Microsoft builds houses and people move in thinking it will be safe. Nearly 24 million people residing in these homes are soon reported sick or dead, causing huge cost and outages. Several independent reports confirm publicly that a service provider is involved in harm. And this provider has been taking little or no significant action to block distribution of harm despite overwhelming evidence; confirmed impact to at least 8 million people. The service provider not only shows no response to public reports of harm, the harm continues to rise.
Microsoft, (now) showing concern about the safety of its homes, tells the court that numerous independent investigations show over 90% harm comes from one service provider. Microsoft asks the court for authority to act on this because, well, logic. They suggest they are in the best position to lead a takeover to continue services without interruption while filtering out harm to tens of millions of people that the court wants to protect. The courts grant this limited authority for the purpose of efficiently cleaning harm.
Unfortunately, this proposal fails. Microsoft’s service has been oversold (surprise) and unable to perform at a level anticipated. Moreover, it turns out to be difficult to prove whether only those causing harm are inconvenienced or also others using the service.
Critics argue as many as 4 million might be inconvenienced (without qualifying as malware or not); but those critics do not measure benefits, or put in perspective of the potentially 24 million harmed over the past year. Critics also argue insufficient notice was given to the service provider before Microsoft moved services to clean them. Remember how I told you to keep in mind that some people said the provider was very responsive to reports of malware? I believe this responsiveness argument backfires on critics of Microsoft. Here’s why:
24 million (worst case) or even 8 million (best case) victims in a year, reported by multiple sources, makes it hard to argue the provider was “responsive” to the issue at hand. They may have been responsive for some particular request, but what did they do about the 24 million problem?
Technically people are right that formal notice is required and necessary. Many in the security community point out however that the provider was a known source of harm being *regularly* notified, which tends to contradict those in the community saying they felt responsiveness adequate for a narrow band of their request. The context often missing from critics of Microsoft is whether reasonable action had been taken in response to public notice about problem in the millions.
A basic review of those who claim responsiveness sufficient suggests the business of remediation and profit from insufficient responses to malware may color their judgment. We can probably balance the question of responsiveness by asking those assessing damage at the full scale of harm whether response was adequate. The courts were maybe considering notification from that angle?
The take-over clearly brought to light some mistakes. I remain skeptical about the action taken, as I said, but I recognize Microsoft for doing what appears to be the right thing. Microsoft obviously needs to be held accountable, just like we would want the DNS service provider to be held more accountable for harm. In fact, it will be interesting to see how harm from the take-over will be demonstrated or documented, as that could actually help Microsoft make their next complaint.
Lessons from this event will help inform how to make improvements for future active defense and set standards of care or definitions of reasonableness. It really kind of annoys me that Microsoft was not able to prove successful their solution for DNS scrubbing. Had they done better engineering or had some proof of service levels, we would be having a completely different discussion right now.
Instead I hear people saying Microsoft was a vigilante (acting without proper authority). That is incorrect. Microsoft asked and was granted authority. Those saying only the government can be an enforcement agent either do not understand public-private relationships or have not thought about the technical challenges (let alone social) of asking the US government to run safe DNS services. Talk about a scary proposition.
Those saying companies are getting a green light to takeover others also are incorrect. Microsoft put together a detailed and compelling complaint with a systemic fix recommendation to reduce a massive amount of harm, linked to multiple current independent sources of research and verification. A green light is very different from the complicated hurdles overcome by Microsoft’s legal team. As in history, their legal prowess unfortunately outdid their engineering.
What this really boils down to is some interesting ethics questions. People are asking for a more trusted Internet, but how do we get there unless someone closest to the harm takes responsibility and proposes solutions within a legal framework (oversight)? Solutions to these types of “wicked problems” require forward thinking in partnerships, as several of us from different industries explained in a recent panel presentation.
So let’s talk about whether Microsoft should be allowed to claim safety of their consumers and users fits within a definition of self-defense. I’m obviously side-stepping the part where Microsoft said they were suffering reputation harm from malware. You can probably tell how I might respond to that claim.
What I really want the community to decide is whether Microsoft can be authorized to perform actions of “self-defense”. They are not policing the Internet. They seem to be asking for the right to block harm to their users in the most efficient, least intrusive way. Perhaps we should ask instead can Microsoft, if we don’t accept a self-defense argument, be authorized to defend consumers and users of theirs who request protection?
It has been very interesting to hear what people think. I really have been doing my best to engage the legal community these past few days and measure as broad a reaction as possible. I am writing this more publicly in the hope to cut through some of the noise about what the security community thinks and point out that even I feel Microsoft is not being fairly credited for reasonable efforts to find cures to some of the problems they helped create.