A detailed review of serious security weaknesses in the 2004 Ohio presidential election system has been posted in the Free Press by co-council on the case.
The system appears to have been under-built and then, as the final tally was run, it switched processing over to an unmonitored and insecure location in a different state operated by a company with a close association to the winning candidate.
The King Lincoln Bronzeville v. Blackwell briefs are cited:
The filing also includes the revealing deposition of the late Michael Connell. Connell served as the IT guru for the Bush family and Karl Rove. Connell ran the private IT firm GovTech that created the controversial system that transferred Ohio’s vote count late on election night 2004 to a partisan Republican server site in Chattanooga, Tennessee owned by SmarTech. That is when the vote shift happened, not predicted by the exit polls, that led to Bush’s unexpected victory.
SmarTech, the location of the servers in Tennessee, is perhaps most infamous for hosting Republican Internet domains — not the sort of environment one would expect to be used for a voting system. It was also later the site used by the Bush White House staff “to evade freedom of information laws by sending emails outside of official White House channels”.
The location and partisanship aside, I find it extremely hard to believe there is not a single firewall let alone a DMZ architecture in the network diagrams. It must be a mistake. Were the vote databases really setup on a flat network?
These details of the network have been revealed only after a fight with Connell, who argued that they should be kept a secret while public — yes, it’s a contradiction.
Connell is refusing to testify or to produce documents relating to the system used in the 2004 and 2006 elections, lawyers say. His motion to quash the subpoena asserts that the request for documents is burdensome because the information sought should be “readily ascertainable through public records request”; but also, paradoxically, because “it seeks confidential, trade secrets, and/or proprietary information” that “have independent economic value” and “are not known to the public, or even to non-designated personnel within or working for Mr. Connell’s business.”
It’s not the first time I have heard this odd and duplicitous argument from a network engineer. A District Attorney (DA) recently said he sent a man to jail for a similar argument in a fight with management. The engineer argued that the government network he was working on was copyrighted (public record) but secret.
The parallels continue. This other man, now in jail, had built a Man in the Middle (MitM) architecture. Connell is accused of creating the exact same security flaw. The Free Press cites “IT security expert Stephen Spoonamore”, who gave a sworn affidavit to the court, that the Ohio presidential network design was intentionally designed to allow a MitM attack.
Until now, the architectural maps and contracts from the Ohio 2004 election were never made public, which may indicate that the entire system was designed for fraud. In a previous sworn affidavit to the court, Spoonamore declared: “The SmarTech system was set up precisely as a King Pin computer used in criminal acts against banking or credit card processes and had the needed level of access to both county tabulators and Secretary of State computers to allow whoever was running SmarTech computers to decide the output of the county tabulators under its control.”
Spoonamore also swore that “…the architecture further confirms how this election was stolen. The computer system and SmarTech had the correct placement, connectivity, and computer experts necessary to change the election in any manner desired by the controllers of the SmarTech computers.”
Given the DA explanation of the other case it is possible the outcome of this one might go the same way. It’s a great example of the reality of insider and domestic threats. While much of the news talks about the foreign threats to US government infrastructure, it is always worth considering that weaknesses in networks may be intentionally created by insiders who seek an unfair advantage.
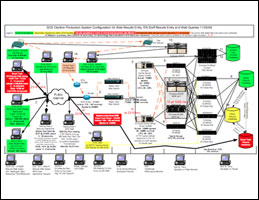

Frightening stuff! Electronic voting seriously worries me, particularly as vulnerabilities can be hidden for seven years (in this case), or never be discovered.
Unfortunately, these sorts of stories aren’t getting enough traction to slow/halt the electronic voting push.