There is a story flying around, thanks to Engadget, that claims “Bernd Marienfeldt and fellow security guru Jim Herbeck” have “discovered” a security issue in the iPhone.
Do they really have to use “guru” as their title? It immediately gives me doubt about the sophistication of the story, but I digress…
They say the issue is that if you connect an iPhone, using the phone’s USB cable, to a computer running Ubuntu 10.04 the phone is mounted and accessible.
The phone can be locked, the phone can be encrypted, but the Linux system will still mount the phone and provide open access to its filesystem.
First, some would say this is clearly a security hole because Apple has “tested and confirmed” that it is one. They bank their argument on the word “confirmed”. Apple also has stated it has no fix and does not plan on having one. This latter statement is what I would like to call your attention to today.
Note that the ability to mount an iPhone in Linux and natively access its files has been a public project under development since 2007. The alpha code was released as iFuse in early 2009 and tested by many people. Towards the end of 2009 iFuse became libimobiledevice and it was so successful several major distributions have included it in their packages:
- openSUSE openSUSE 11.0, 11.1, 11.2, Factory
- Fedora Fedora 12+ (Packages in the official repositories)
- Mandriva Mandriva (Packages are available in “Cooker”)
- Ubuntu (Karmic), Ubuntu Lucid (Packages in the official repositories)
It is from this context that I find it a bit odd that “security gurus” have tried to claim “discovery” of this functionality and brand it a flaw. While the passcode has never prevented me from mounting the iPhone in Linux the libmobiledevice project says this has not been their experience.
27.05.2010: Some security sites report that even passcode enabled devices get auto-mounted. We could not reproduce this yet. However it might point at some bug during boot in the iPhone OS. Accessing a passcode enabled device the first time does not work in our tests as one would expect. Devices taking more time booting might be affected though, on any OS.
Maybe there is an intermittent issue here, but I am able to reproduce it on all my Linux systems. In fact this is the only way it has worked for me over many months.
I considered the iPhone insecure for this as well as many other reasons. That is why I believe the real issue here boils down to whether you consider the iPhone a secure device or not. Do you?
If you are in the camp that thinks the iPhone can be a secure device, then once again you are in for a surprise. It is not, and this is definitely not the first time this has been discussed openly. Anyone with a computer and a Linux CD has been able to access everything on your phone for over a year. Moreover, there has been a rash of attacks that target people who are actively using the iPhone. Thieves know that if they get the phone away from the owner when it is not locked they have easy access to the data; owners should know this too.
If you are in the camp that does not think the iPhone can be a secure device…you are right. In fact, you might even work for Apple and be one of the people who said “we have no fix and no plan to make a fix” to any number of the control points for data confidentiality.
In other words the absence of a plan to make a fix says to me that Apple does not see this as a serious flaw, let a lone a flaw at all. They perhaps just confirmed that Linux is able to read the filesystem properly in the same way that a thief who grabs the phone can use apps and access data.
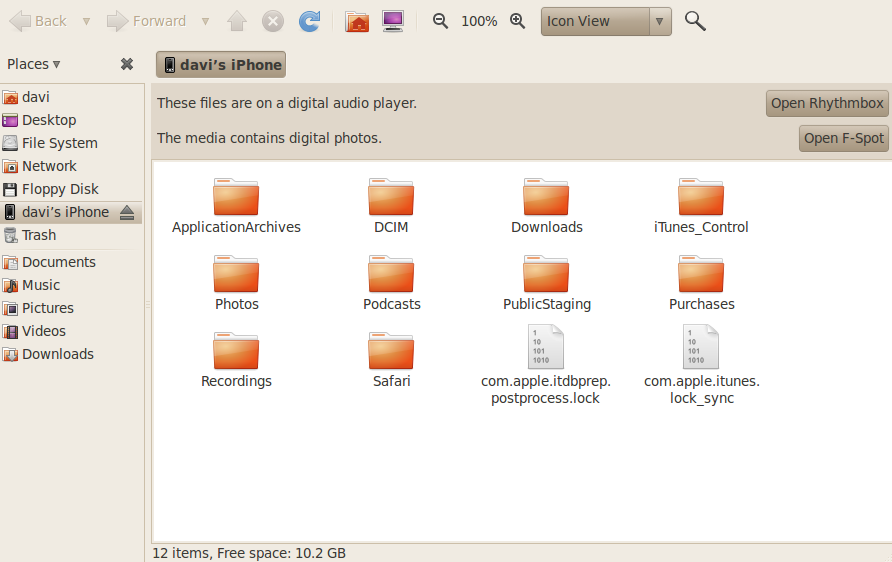
Here is what anyone who plugs an iPhone into a Linux computer can see:
1) Plug the iPhone into the computer using the Apple USB cable that comes with the phone. You will see it appear as a mounted filesystem (Apple File System or AFS) on the desktop.
2) Then you will be prompted with two dialog boxes, one for music and one for photos:
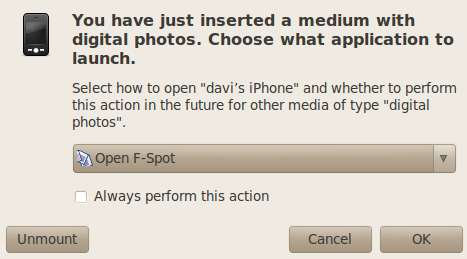
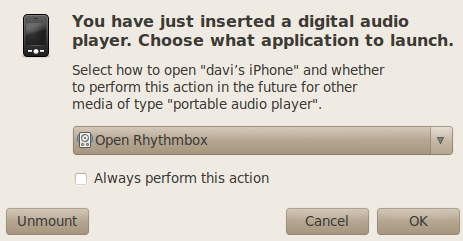
3) You can choose to browse the filesystem from those dialog boxes, instead of opening applications to manage music and photos. Or you can cancel the dialog and just open the filesystem to browse from the desktop. Either way, full access to unencrypted data without needing to know the PIN. Surprised?
I downloaded and installed Ubuntu 10.04 the day it was released and the iPhone has always appeared this way to me. It did not seem to me that my data was any more exposed than I had already thought.
Perhaps I am giving the Apple team too much leeway when I say there is no new issue here and no fix needed, but I also do not think anyone should have seriously considered the iPhone to be a secure or safe device. It is highly unsafe at any speed. News?
Even in a physical security review I immediately found it designed to be incredibly fragile and prone to disaster. At least once a week I see a twitter from someone about an iPhone failure. Not news.
Perhaps for the same reason Apple put the infamous and unreliable sensitive water sensors in the iPhone that void your warranty when triggered, no one should operate one under the assumption that this device is designed to protect data without significant outside controls and enhancements.
Giant foam cases, screen covers, vacuum sealed bags…the list goes on and on for things to buy to protect the phone. None of it seems to be from Apple. Likewise we have known for years that proper encryption and authentication for the filesystem is something you will not be getting when you purchase an iPhone. I do not feel knowing this about Apple products can really be called enlightenment.
The syllable gu means shadows
The syllable ru, he who disperses them,
Because of the power to disperse darkness
the guru is thus named.