Welcome to SF everyone! As the RSA Conference week begins, which really is a cluster of hundreds of security conferences running simultaneously for over 40,000 people converging from around the world, I sometimes get asked for local curiosities.
As a historian I feel the pull towards the past, and this year is no exception. Here are three fine examples from hundreds of interesting security landmarks in SF.
Chinese Telephone Exchange
During a period of rampant xenophobia in America, as European immigrants were committing acts of mass murder (e.g. Deep Creek, Rock Springs) against Asian immigrants, a Chinese switchboard in 1887 came to life in SF (just before the Scott Act). By 1901 it moved into a 3-tier building at 743 Washington Street. Here’s a little context for how and why the Chinese Telephone Exchange was separated from other telephone services:
Today when you visit Chinatown in SF you may notice free tea tastings are all around. This is a distant reminder of life 100 years ago, even for visitors to the Chinese Telephone Exchange, as a San Francisco Examiner report describes in 1901:
Tea and tobacco are always served to visitors, a compliment of hospitality which no Chinese business transaction is complete
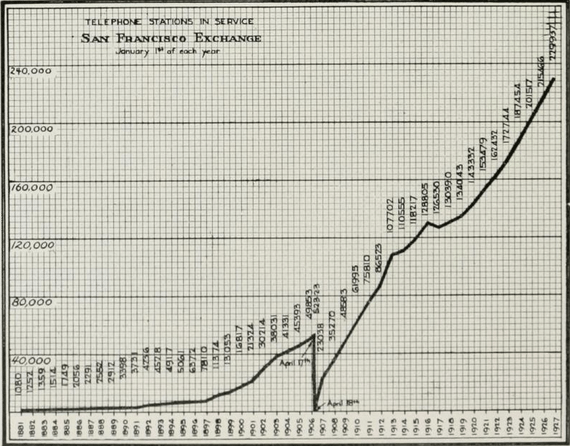
At it’s peak of operation about 40 women memorized the names and switching algorithms for 1,500 lines in five dialects of Chinese, as well as English of course. Rather than use numbers, callers would ask to be connected to a person by name.
The service switched over 13,000 connections per day until it closed in 1949. Initially only men were hired, although after the 1906 earthquake only women were. Any guesses as to why? An Examiner reporter in 1901 again gives context, explaining that men used anti-competitive practices to make women too expensive to hire:
The Chinese telephone company was to put in girl operators when the exchange was refitted, and doubtless it will be done eventually. The company prefers women operators for many reasons, chiefly on account of good temper.
But when the company found that girls would be unobtainable unless they were purchased outright, and that it would be necessary to keep a platoon of armed men to guard them, to say nothing of an official chaperon to look after the proprieties, the idea of girl operators was abandoned.
“They come too high,” remarks the facetious general manager, “but in the next century we’ll be able to afford them, for girls will be cheaper then.”
Pacific Telephone Building
One of the first really tall developments in SF, which towered above the skyline (so tall it was used to fly weather warning flags and lights) for the next 40 years, were the Pacific Telephone offices. At 140 Montgomery Street, PacTel poured $4 million into their flagship office building for 2,000 women to handle the explosive growth of telephone switching services (a far cry from the 40 mentioned above at 743 Washington Street).
By 1928, the year after 140 New Montgomery was completed, the San Francisco Examiner declared “with clay from a hole in the ground in Lincoln, California, the modern city of San Francisco has come.”
It was modeled after a Gottlieb Eliel Saarinen design that lost a Chicago competition, and came to life because of the infamous local architect Timothy Pflueger. Pflueger never went to college yet left us a number of iconic buildings such as Olympic Club, Castro Theater, Alhambra Theater, and perhaps most notably for locals, a series of beautiful cocktail lounges created in the prohibition years.
AT&T Wiretap
Fast-forward to today and there are several windowless tall buildings scattered about the city, filled with automated switched connecting the city’s copper and fiber. One of particular note is 611 Folsom Street, near the latest boom in startups.

Unlike the many years of American history where telco staff would regularly moonlight by working for the police, this building gained attention for a retired member of staff who disclosed his surprise and disgust that President Bush had setup surreptitious multi-gigabit taps on telco peering links.
“What the heck is the NSA doing here?” Mark Klein, a former AT&T technician, said he asked himself.
A year or so later, he stumbled upon documents that, he said, nearly caused him to fall out of his chair. The documents, he said, show that the NSA gained access to massive amounts of e-mail and search and other Internet records of more than a dozen global and regional telecommunications providers. AT&T allowed the agency to hook into its network at a facility in San Francisco and, according to Klein, many of the other telecom companies probably knew nothing about it.
[…]
The job entailed building a “secret room” in an AT&T office 10 blocks away, he said. By coincidence, in October 2003, Klein was transferred to that office and assigned to the Internet room. He asked a technician there about the secret room on the 6th floor, and the technician told him it was connected to the Internet room a floor above. The technician, who was about to retire, handed him some wiring diagrams.
“That was my ‘aha!’ moment,” Klein said. “They’re sending the entire Internet to the secret room.”
[…]
Klein was last in Washington in 1969, to take part in an antiwar protest. Now, he said with a chuckle, he’s here in a gray suit as a lobbyist.
In some sense we’ve come a long way since 1887, tempting us to look at how different things are from technological change, and yet in other ways things haven’t moved very far at all.