History of American prosecution of Nazi sympathizers shows JD Vance and Pete Hegseth have entered seditious territory
The Precedent
In 1944, the U.S. government brought sedition charges against 30 Americans under the Smith Act. Their crime: membership in the America First Committee and publishing “seemingly pro-German writings” that prosecutors said were part of “a gigantic conspiracy with German and Nazi officials.” The charges established the standard: even passive support for Nazis through speech was considered seditious.

America First in 1940 simply meant a white supremacist campaign to enable Hitler, as documented in the Yale “college” movement’s archives at the Gerald Ford museum.

The defendants of America First said they opposed the war against Hitler, and they espoused Hitler’s rabid hate speech. They plotted overthrowing the American government, they held mock trials of the American President and of course they published materials questioning U.S. involvement in stopping Hitler.
America First thus attempted to destroy democracy by passively supporting the Nazi cause through speech and published materials. And rather than identify themselves openly and positively as Nazis, they claimed negatively that they were opposed to anyone antifa (anti-Hitler).

Their more direct attempts to overthrow the government in 1933 failed, which is arguably why they became so negative/passive. They didn’t overtly threaten political opponents with gas chambers, and they didn’t say “I love Hitler.” They said: stop trying to stop Hitler.
For this passive role, they faced five to twenty years in prison. I mean, many of them did but not Gerald Ford who went from seditious college hate groups to becoming the President decades later (when Nixon was forced out), if you see the problem already.
By 1996 the official America First candidate for President, Ralph Forbes, was openly campaigning as a Nazi, and he received under 1,000 votes. America First was so extreme, thoroughly crushed as a brand of fascism, that it had to rebrand itself into “Christian Patriot” ranchers and cowboys.
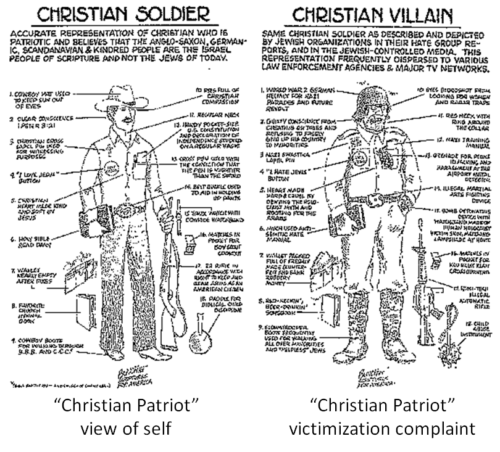
Let me be more clear. Forbes was the “America First Party” candidate in 1996, campaigning as former leader of the KKK and American Nazi Party. He had rapidly advanced to the rank of captain and commander of its western division under George Lincoln Rockwell, founder of the American Nazi Party, as there wasn’t really much competition. He had served also as the campaign manager for David Duke’s disasterous Populist Party (KKK) campaign for the Presidency.

THAT was, and still is, what should be understood as America First.

The Legal Standards
The Smith Act very clearly criminalized America First to block its intended outcomes:
- Conspiring to “impair the loyalty of the armed forces”
- Advocating overthrow of government by force
- Speech intended to cause insubordination or obstruct military recruitment
The constitutional framework has not changed since 1944. Three Supreme Court cases, however, have been argued to define boundaries:
Chaplinsky v. New Hampshire (1942): Fighting words that “by their very utterance inflict injury” are unprotected.
Brandenburg v. Ohio (1969): Speech loses First Amendment protection when “directed to inciting or producing imminent lawless action and is likely to incite or produce such action.”
Virginia v. Black (2003): True threats—”statements where a speaker means to communicate a serious expression of intent to commit unlawful violence”—are not protected speech.
These standards have made prosecution of Nazis harder than the 1944 Smith Act, not easier. The bar for sedition is higher now than when America quickly jailed Nazi sympathizers, which is arguably why America First (waving their red, white and black hats and flags) suddenly openly campaigned itself into control of the White House.

The question isn’t whether these Republican actions meet historical thresholds for sedition—they clearly exceed them. The question is whether America in 2025 still has the institutional will to enforce laws it once considered fundamental to national security.
The Vance Standard
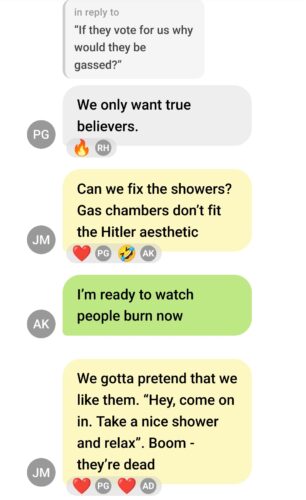
This rapid decline of American protection against Nazis helps explain the headlines in 2025. Young Republican leaders—including government officials, state legislators, and congressional staffers—sent 2,900 pages of messages showing:
- White supremacist symbol 1488 used repeatedly
- “Great. I love Hitler” with enthusiastic reactions
- “Everyone that votes no is going to the gas chamber”
- 251+ racial slurs and dehumanizing language
- Explicit support for Republicans who “support slavery”
- Discussions of rape, violence, and “psychological torture methods”
This isn’t passive support like during WWII. This is now very active promotion of hateful violent Nazi ideology combined with explicit threats against political opponents by people with government authority and organizing capacity.
Vice President JD Vance’s response reveals the well known America First pattern: dismissed Nazism as “college group chat” and told Americans not to “pearl clutch” about his fellow Republicans who advocate for rapid political assassination and genocide.
Under the 1944 standard—even passive support for Nazis—every person in those chats would face sedition charges. Active sabotage conviction would mean execution.

Under the 2025 standard—active threats of violence—they meet the legal threshold for prosecution.
Under any standard—the Vice President is providing institutional cover for seditionists.
When Vance:
- Minimizes documented Nazi symbolism and genocide threats as harmless banter
- Simultaneously labels Democrats a “domestic terrorism movement”
- Calls universities “the enemy” requiring “aggressive attack” for opposing Nazism
- Uses government power to order FBI/Treasury crackdowns on political opponents without evidence
…he meets the elements of seditious conspiracy under 18 U.S. Code § 2384: using force or intimidation to “oppose,” “prevent, hinder, or delay the execution” of U.S. law.
The laws against domestic terrorism that he’s actively obstructing?
Those are the laws his self-admitted allies are violating in those chats. But Vance’s cover extends beyond protecting just the Young Republicans actively promoting Nazism.
The Hegseth Standard
Defense Secretary Pete Hegseth’s actions reveal an even more direct violation of the Smith Act’s prohibition on “conspiring to impair the loyalty of the armed forces.”
Hegseth ordered all service members to watch his speech demanding they conform to his political ideology or resign. Active-duty service members describe this as “a loyalty test” and warn “it’s scary how many of these higher-ups are following blatantly illegal orders.”
Military legal scholars at Yale Law School warn that Hegseth is attempting to “subordinate our national defense to the personal, political and social agendas of a commander-in-chief who prizes personal loyalty above the military’s commitment to our nation and Constitution.”
The evidence of impairing military loyalty is systematic:
- Fired Chairman of the Joint Chiefs Gen. CQ Brown and dozens of generals/admirals in what officials call a “purge”
- Told podcast audiences “any general that was involved in any of that DEI woke shit has got to go”
- Ordered 20% cuts to four-star generals and admirals—eliminating roughly 100 senior officers
- Fired the Army and Air Force’s top judge advocates general to avoid “roadblocks to orders”
- Commissioned his personal lawyer—who defended a Navy SEAL accused of war crimes—to overhaul military legal counsel to “approve more aggressive tactics and take a more lenient approach to those who violate the law of war”
- Summoned 800+ generals and admirals from worldwide posts to Quantico for a loyalty speech, with defense officials calling it “embarrassing” and questioning why senior officers had to be “pulled away from their missions to listen to hours of political grievances”
This is not reforming the military. This is systematically purging officers based on political ideology and demanding personal loyalty over constitutional oath.
Under the 1944 Smith Act standard, Hegseth would face immediate prosecution for conspiracy to impair military loyalty—the exact charge brought against America First members who merely published anti-war materials.
Hegseth is actively restructuring military command to prioritize loyalty to Trump over the Constitution, firing officers who resist, eliminating legal oversight, and forcing remaining officers to publicly affirm his political agenda.
The Vice President provides cover for this too.
The LaGuardia Standard
In the 1930s, New York City Mayor Fiorello LaGuardia faced Nazi infiltration of law enforcement. His response was unequivocal: he issued orders to all city departments prohibiting association with fascist organizations.

As documented in the historical record, when faced with evidence of Nazi organizing, LaGuardia took aggressive action in order to declare NYC free of Nazism. He refused professional licenses to German nationals invoking treaty rights, arguing “it is well known that American citizens of the Jewish faith have been discriminated against in Germany.” He issued criminal libel charges against anti-Semitic propagandists (e.g. Edmondson). He canceled German steel contracts for city projects.
Most importantly: LaGuardia never dismissed even the slightest Nazi organizing as harmless.
LaGuardia understood how officers sworn to uphold the Constitution cannot simultaneously pledge loyalty to movements seeking to overthrow it. This was considered a fundamental principle of democratic governance.
Hegseth has inverted this principle. Rather than purge those with authoritarian loyalties, he purges those loyal to the Constitution. Rather than prohibit association with extremist ideology, he demands conformity to it.
Under the LaGuardia standard—enforced against individual police officers—Hegseth’s systematic restructuring of military command to prioritize personal loyalty over constitutional oath would warrant immediate removal and prosecution.
Sedition Question
In 1944, America prosecuted citizens for even passively supporting Hitler through speech.
In 2025, government officials actively spread Nazi symbolism and threaten opponents with mass murder (e.g. Hitler rapidly jailed both his supporters and opponents to execute anyone with power). And the Vice President very openly and unashamedly provides cover, while accusing victims of being the threat.
MAGA tells us to go backwards in time, which means the 1942 America First active seditionists were executed, and the 1944 America First passive seditionists deserved jail.
Given these standards that America has applied to Nazi sympathizers, what are Vance and Hegseth… again?