When Donald Trump floated his plan to acquire Greenland, many dismissed it as another bizarre outburst from a president who treats geopolitics like a reality TV show. But this obsession with the Arctic reveals something far more sinister: the latest chapter in a colonial playbook refined over centuries. Trump’s rhetoric about Greenland follows a template so precise it could have been plagiarized from Andrew Jackson’s diary, only with SpaceX snake-oil slides replacing speeches on Manifest Destiny.
Six years from 2016 we will be colonizing Mars? Let me get my calculator out.
Beta Test Invasions: Florida to Hawaii
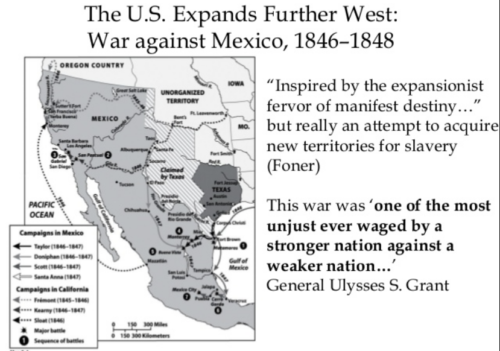
The American colonial playbook was first tested in Florida in the 1810s. Jackson’s campaign in Florida set the model: delegitimize indigenous governance, create security pretexts, deploy overwhelming force, and most importantly, ignore legal constraints. By the time Texas was annexed in 1845, the “security necessity” argument was fully polished. California followed in 1846, and Hawaii in 1893, each expansion a refinement of the formula. It was no longer just about acquiring land—it was about perfecting demographic engineering and entrenching settler dominance for rapid value extraction and centralization.
Every time you look at the common banana-split, consider how it advertises to this day the sweet spoils of American militant imperialist lies and abuse to unjustly assert territorial domination over indigenous groups. 
Mussolini’s Attention-Seeking Upgrade
In 1935, Mussolini’s invasion of Ethiopia was a chilling echo of America’s colonial methods, but with a fascist twist. He studied America’s expansionist playbook, applying it to Ethiopia and justifying his actions with the same rhetoric of “civilizing” indigenous populations. His campaign wasn’t just awful murderous barbarism and brutality—he setup a test case to prove that the American model could be scaled abroad under intentionally misleading propaganda about market dynamics or keeping the peace.
In a speech before the Senate tonight on the nation’s foreign affairs, Premier Mussolini declared that Italy is an imperialist nation. But, he added, her imperialism, far from being aggressive, explosive or in preparation for war, is the peaceful, intellectual, cultural and economic expression of a great nation arriving somewhat late at its maturity.
His rhetoric about Ethiopia’s “strategic necessity” mirrored the justifications of American territorial expansion, showing that the template was global and adaptable. After military invasion, waves of geologists and colonial planners were pushed into rapid settlement among the tens of thousands of dead.
Hitler’s Industrialized Application
Hitler took this American template and Mussolini’s systematic approach to deception, scaling it for even more rapid and industrialized repetitive conquests. The Sudetenland in 1938 was his “Florida,” a first step where he proved the world would acquiesce. By the time Poland was invaded in 1939, international resistance had been so thoroughly debunked that it resembled a wet paper bag. Nazi territorial ambitions weren’t impulsive—they were calculated, a direct line from the aggressive bully patterns learned and facilitated over time from Jackson to Mussolini.
- Carroll Kakel “The American West and the Nazi East”
- James Whitman “Hitler’s American Model”
- Edwin Black “IBM and the Holocaust”
Trump’s Digital Copy
Trump’s focus on Greenland represents the latest evolution of this colonial playbook, now fused with two technology leaders of the modern surveillance state (Thiel and Musk). His rhetoric hits every historical note: delegitimize indigenous governance (“nobody knows if they have any right”), manufacture security pretexts (“strategic necessity”), threaten overwhelming force. But now, there’s a terrifying new layer: the tools of AI and demographic control like something straight out of 1980s South Africa.
Unlike Jackson’s era, where expansion meant physical occupation, today’s colonialism seeks to control populations through data, surveillance, and automated systems of the infamous “BOSS” watching everyone to keep apartheid running.
Trump’s vision for Greenland isn’t just about resources; it’s about building a new kind of colony—one governed by digital tools that manage borders, movements, and populations. The modern version of manifest destiny is less about useable land and more about establishing an Aryan Nation fantasy of repopulation by “landing” and expanding a technology driven existence.
Greenland Fits Pattern
Greenland is positioned as a test case, much like how Florida was being treated in 1835, or Ethiopia 100 years later in 1935. The playbook has been refined over time—each expansion and conquest a proving ground for the next. Now, Greenland serves as the proving ground for a new era in expansive colonization under one white man. Canada being called a state of the U.S. in Trump social media is like looking at a racist pamphlet from Musk’s grandfather, who envisaged exactly such expansive Technocracy maps in the 1940s. Trump’s son, arriving in Greenland with MAGA hats in tow, is not just a historical echo; it’s a systematic replication of tactics that have worked before. Just look at Mussolini’s entourage to Ethiopia before invasion.
Mussolin sends his sons Bruno and Vittorio to Abyssinia / Big drafts leave Italy as war clouds thicken (1935)
Trump Stakes Aren’t Rare
This iteration of the colonial playbook is more dangerous than its predecessors. Where past empires used brute force, today’s empire will use technology to prevent resistence and control populations from the inside out. The tools of surveillance, AI, and automated systems are all being tested, and once in place, they will offer a level of control that earlier generations of colonizers could not have imagined.
When Trump talks about Greenland surrounded by tech billionaires, he’s not just channeling Jackson’s territorialism; he’s upgrading it for the AI age. The entitled certainty that allowed colonizers to take land is now coupled with the power to monitor, manipulate, and control populations on a global scale.
This week in 1937, Italian Fascists and colonizers began a three-day massacre in Addis Ababa, killing up to 20,000 Ethiopians. The slaughter is all but ignored in today’s Italy…
Recognition and Repudiation
The historical pattern is clear: after Florida came Texas, after Ethiopia came broader conquest, and after the Sudetenland came Poland. Each failure trained the world to believe resistance was futile except at massive cost of all out war. Trump’s Greenland obsession isn’t a fluke—it’s the next step in a playbook refined over centuries to abuse power.
The real question is whether we’ll recognize this pattern in time. When someone tells you they can “shoot somebody on Fifth Avenue” without consequence, don’t look surprised when it turns out to be the King of Denmark. The jump from “grab them by the pussy” to “grab them by the glacier” is not as far as it seems, and the tools for total control are already in motion.
The world shamefully didn’t register Haile Selassie’s clarion and accurate warning in 1936, let alone Silas Soule in 1864. Now, as Trump’s son brings MAGA hats to Greenland like Mussolini’s boys to Ethiopia, we face a choice: recognize the pattern or watch it repeat at faster pace and greater tragedy.
From this:
Mussolini’s long-expected invasion of Abyssinia began at dawn yesterday… Two of the bombers were reported to be piloted by Mussolini’s sons, Vittorio, aged 19, and Bruno, aged 18…
To this:
Greenland coming in hot…” Trump Jr. said in a post on the social platform X that featured video of the cockpit of an airplane flying over frozen topography.
The template is painfully clear: from Jackson’s Indian Removal to Musk’s family dreams of white settler colonies in Canada, South Africa, and Rhodesia, to today’s technocratic visions of controlled breeding programs in Arctic compounds. It was never just about land – it was always about engineering white demographic birthing fantasy through illegal compound distribution. Mars is the marketing pitch; Greenland is the just the latest aspirational target. Same abusive playbook, just with more emojis.




