The U.S. is very confidently accusing Iran of attacking Albania, based on yesterday’s report by Microsoft about Microsoft’s usual software vulnerabilities and mis-configurations.
Microsoft assessed with high confidence that on July 15, 2022, actors sponsored by the Iranian government conducted a destructive cyberattack against the Albanian government, disrupting government websites and public services. At the same time, and in addition to the destructive cyberattack, MSTIC assesses that a separate Iranian state-sponsored actor leaked sensitive information that had been exfiltrated months earlier. Various websites and social media outlets were used to leak this information. […] A group that we assess is affiliated with the Iranian government, DEV-0861, likely gained access to the network of an Albanian government victim in May 2021 by exploiting the CVE-2019-0604 vulnerability on an unpatched SharePoint Server, administrata.al (Collab-Web2.*.*), and fortified access by July 2021 using a misconfigured service account that was a member of the local administrative group. Analysis of Exchange logs suggests that DEV-0861 later exfiltrated mail from the victim’s network between October 2021 and January 2022.
The report unfortunately is not titled “What are you even doing running Sharepoint in 2021” and instead uses this far more provocative line:
Microsoft investigates Iranian attacks against the Albanian government
Just a decade ago many experts in the security industry warned against investigations being so overtly bold or confident with their attribution statements. The fear was rooted in dubious logic that someone could make a mistake and therefore shouldn’t even try.
I mean if that was sound logic Sharepoint would have never been released to the public. Ok, maybe there’s some truth to that logic.
But seriously, anyone in any history 101 class knows you can’t let perfect be the enemy of good when writing reports about what happened in the past. Of course you can get attribution wrong, which is in fact why you should try hard and make sure you do it well.
It feels like a very long ago time ago (but really only 2014) that I gave a counter-argument to fears about uncertainty, in a presentation to incident response teams in Vienna, Austria basically saying it’s time for attribution.

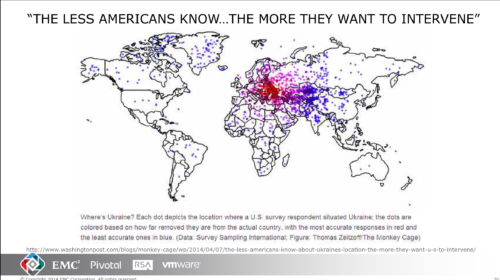
Looking back at my slides, honestly I think I tried too hard to make data integrity funny. Attribution is less complicated by some unique thing about computers than it is by things about people like this: Americans are more likely to want to intervene in places they can’t find on a map (click to enlarge and have a sad laugh).
Here’s another one, where I poked fun at FireEye for making very crude and rube attribution mistakes and surviving (they’re still in business, right?).

Now look how far the world has come!
Microsoft shakes heavy doses of political science into its computer forensics reports like it’s powdered sugar on a Turkish delight.
- The attackers were observed operating out of Iran
- The attackers responsible for the intrusion and exfiltration of data used tools previously used by other known Iranian attackers
- The attackers responsible for the intrusion and exfiltration of data targeted other sectors and countries that are consistent with Iranian interests
- The wiper code was previously used by a known Iranian actor
- The ransomware was signed by the same digital certificate used to sign other tools used by Iranian actors
[…] A group that we assess is affiliated with the Iranian government, DEV-0861…
[…] The geographic profile of these victims—Israel, Jordan, Kuwait, Saudi Arabia, Turkey, and the UAE—aligns with Iranian interests and have historically been targeted by Iranian state actors, particularly MOIS-linked actors.
[…] The cyberattack on the Albanian government used a common tactic of Iranian state sponsored actors…
[…] The wiper and ransomware both had forensic links to Iranian state and Iran-affiliated groups. The wiper that DEV-0842 deployed in this attack used the same license key and EldoS RawDisk driver as ZeroCleare, a wiper that Iranian state actors used in an attack on a Middle East energy company in mid-2019.
[…] Multiple other binaries with this same digital certificate were previously seen on files with links to Iran, including a known DEV-0861 victim in Saudi Arabia in June 2021
[…] The messaging, timing, and target selection of the cyberattacks bolstered our confidence that the attackers were acting on behalf of the Iranian government. The messaging and target selection indicate Tehran likely used the attacks as retaliation for cyberattacks Iran perceives were carried out by Israel and the Mujahedin-e Khalq (MEK), an Iranian dissident group largely based in Albania that seeks to overthrow the Islamic Republic of Iran.
[…] The messaging linked to the attack closely mirrored the messaging used in cyberattacks against Iran, a common tactic of Iranian foreign policy suggesting an intent to signal the attack as a form of retaliation. The level of detail mirrored in the messaging also reduces the likelihood that the attack was a false flag operation by a country other than Iran.

Done and dusted. Need I continue?
It is nice to see such definitive and detailed work about attribution as if it’s a normal investigation with regular analysis methods… but it’s even nicer to read Albania has announced they’re cutting ties with Iran. And then… to see the U.S. follow-up with announcements about sanctions, it’s like why didn’t Microsoft start doing this way back in 1986 instead of for decades completely ignoring security as a get-rich scheme?