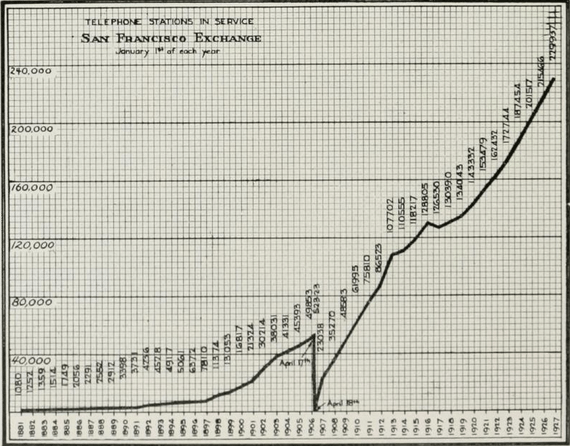
Pete Blaber’s book “The Mission, the Men, and Me: Lessons from a Former Delta Force Commander” gets a lot of rave reviews about business practices and management tips.
Pete Blaber’s book “The Mission, the Men, and Me: Lessons from a Former Delta Force Commander” gets a lot of rave reviews about business practices and management tips.
It’s hard not to agree with some of his principles, such as “Don’t Get Treed by a Chihuahua”. This phrase is a cute way of saying know your adversary before taking extreme self-limiting action.
Who would disagree with that?
But I’m getting ahead of myself. The book begins with a story of childhood, where Pete reflects on how he topographically mastered his neighborhood and could escape authorities. That gives way to a story of his trials and tribulations in the Army, where during training he was tested by unfamiliar topography and uncertain threats.
It is from this training scenario that Pete formulates his principle to not jump off a cliff when a pig grunted at him (sorry, spoiler alert).
Maybe a less cute and more common way of saying this would be that managers should avoid rushing into conclusions when a little reflection on the situation is possible to help choose the most effective path. Abraham Lincoln probably said it best:
Give me six hours to chop down a tree and I will spend the first four sharpening the axe.
How should someone identify whether they are facing only a Chihuahua-level threat, given their other option is to run and blindly climb a tree?
Pete leaves this quandary up to the reader, making it less than ideal advice. I mean if in an attempt to identify whether you are facing a Chihuahua, wild pig or a bear you get mauled to death, could you sue Pete for bad advice? No, because it was a bear and instead of being up a tree you are dead.
Michael Shermer covered this dilemma extensively in his book “The Believing Brain: From Ghost and Gods to Politics and Conspiracies — How We Construct Beliefs and Reinforce Them as Truths.”
Given his lessons learned in joining the Army, Pete transitions to even more topographical study. He masters mountain climbing with a team in harsh weather. It’s a very enjoyable read.
I especially like the part where money is no object and the absolute best climbing technology is available. There’s no escaping the fact that the military pushes boundaries in gear research and keeps an open mind/wallet to technology innovations.
From there I can easily make the connection to the climax of the book, where he leads a team on a topographically challenging mission and minimizes their risk of detection. It really comes full circle to his childhood stories.
However, there are a few parts of the book that I found strangely inconsistent, which marred an otherwise quick and interesting read.
For example, Pete makes a comment about religion and culture that seems uninformed or just lazy. He refers to Cat Stevens as the “most renowned celebrity convert to Islam”:

I’m not claiming to be an expert in celebrity status or Islam, just saying it should be kind of obvious to everyone in the world that Muhammad Ali (nee Cassius Clay) is far more renowned as a celebrity convert to Islam. I don’t think Cat Stevens even breaks into top ten territory.
Afer winning the Olympics in 1960, the hugely popular Clay not only went on to convert he also refused serving US armed forces in Vietnam because a “minister in the religion of Islam”. As the FBI puts it in their release of surveillance files:
…famed Olympian, professional boxer and noted public figure. This release consists of materials from FBI files that show Ali’s relationship with the Nation of Islam in 1966.
Pete’s comment about the popularity of Cat Stevens suggests that despite the no-holds-barred approach to piles of rock, he may lack knowledge in human topics essential to conflicts he was training to win. A quick look at discussion of Islamic celebrities backs up this point:
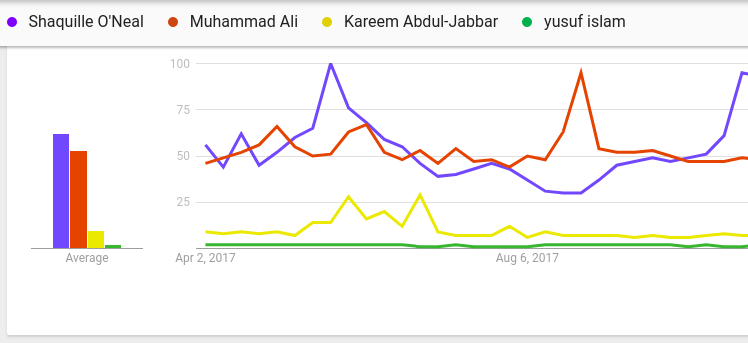
Pete was wandering on that flat line at the bottom while giant mountains of culture stood right above him, unexplored, despite his access to the best tools. When Pete doesn’t mention any ethnic or religious diversity values in childhood it perhaps comes as foreshadowing, leaving him inexperienced and unprepared his whole life to properly identify an Islamic Chihuahua.
Perhaps also important to note, in terms of celebrity status, white Muslims are the most prevalent in America…
No racial or ethnic group makes up a majority of Muslim American adults. A plurality (41%) are white… and one-fifth are black (20%).
The famous three-time Golden Globe-winning actor Omar Sharif, for example, was a Catholic who converted to Islam in 1955.

There are at least two more examples of this class of error in the book. I may update the post with them as I have time.