The Central Intelligence Agency (CIA) use of information warfare is often discussed and sometimes cited, yet is not clearly linked to any present day debates about authorization regarding “cyber” active-defense (offense). This becomes confusing as the intelligence community may be in competition with the military over emerging demand for modern hacking capabilities, particularly in cases outside the U.S. government’s own systems.
The clandestine nature of ongoing intelligence missions makes it difficult to expose and examine fully any examples, which unfortunately means the most current relevant trade craft goes un-examined while debates rage about who should be doing it. Perhaps an investigation of history would help here with direction and regulation.
A case easily can be made that information warfare options today are a derivation of 1930s experimentation and 1940s deployments, which means the CIA creation story might be extremely relevant to today’s Title 10 / Title 50 debates.
It thus is increasingly important for American “cyber” policy-makers to spend the time to reflect on history and consider international political winds of the 1930s. This was when a modern purpose and scope for information gathering was established for cogent analysis and dissemination, as well as the basis established for covert operations against foreign adversaries.
Take for example when Franklin D. Roosevelt (FDR) initiated clear steps around central intelligence operations in the aftermath of his U.S. presidential campaign victory, with an eye on both a domestic coup attempt (Business Plot or White House Putsch) as well as tensions spreading in Europe and Asia.
During the 1932 U.S. presidential campaign William Hearst allowed his expansive media empire to circulate Hitler’s writing and spread white nationalist’s ideology in America.
Hearst defended his actions by expressing he had fear of socialism and was a believer in the false depictions by Hitler. To put it briefly, FDR won the Presidency in spite of an American media giant’s attempts to stir up Nazi sympathizers and groups of “devoted nationalist followers to threaten and beat up leftists”. 1
Later Hearst admitted a change of heart so by 1938 he had reversed position on Hitler, allegedly because the Nazi Kristallnacht facts being reported by his papers. However for FDR the information warfare die already had been cast by 1932; foreign military intelligence operations were correctly identified in undermining American stability. FDR after winning the election was immediately faced with how to put in place national security measures to counteract dangerous information warfare threats to global democracy.
A rarely referenced event in this context, yet still very important to this history of information warfare, is the 1934 establishment of a Federal Communication Commission (FCC). Overtly the FCC is described as a means to break up monopolization in American communications. It also should be seen as a disinformation control, in direct and stark opposition to what American and British officials had heard reports of in Nazi Germany. Hitler’s volksgemeinshaft meant a total centralization of communications under a state propaganda ministry, which manifested in April 1934 using the Reich Radio Company. 2
The 1934 move towards decentralized regulated communications not only was a reaction to Hearst’s role in 1932, but also appears to have been a reasonable means to neutralize future national security disaster (prevent broadcast subversion and manipulation by foreign military intelligence or domestic collaborators). FDR early on understood how Nazi military intelligence ability to control, disrupt or manipulate informational infrastructures was as decisive a factor as weapons superiority, with respect to democracy being protected from fascist aggression.
How better to defend both U.S. informational infrastructure against powerful yet naive Nazi sympathizers than just regulatory acts like the FCC? This is where the story of the CIA really begins, as FDR not only was exploring how to use his authority to block foreign information attacks, he initiated U.S. offensive capabilities.
The parallel to modern debates is interesting because critics of offensive hacking today often point to American infrastructure having a weak defensive posture.
Here we see FDR’s creation of offensive capabilities came after he had pushed improvements to defensive capabilities through a new FCC. It begs the question whether creating any sort of “cyber” equivalent to an FCC role today would placate critics of offensive operations. Perhaps even a hybrid third agency from the FCC and DoJ would work? The FCC notably predates all the deterrence theorists of WWII and after, playing a more subtle and often overlooked role in the conflict.
Offensive capabilities may be proposed as an alternative to improving resilience to attacks, yet balance makes sense and people today should really consider whether and how FCC and CIA both were created to deal with Nazi threats to democracy.
During the summer of 1940, at a time when there was no American clandestine service organization in operation (as evidenced by intelligence gaps in the 1936 Japanese sinking of USS Panay), FDR sent a special envoy to London. The President wanted to know whether unusually lackluster resistance to violent Nazi incursions in Europe was related to information warfare measures. FDR asked his envoy to assess whether “demoralizing propaganda and internal subversion by Nazi sympathizers” had been undermining national security of states targeted by Hitler. 3
The President obviously needed to curtail the influence of German military intelligence service information campaigns, and measure the effects of domestic espionage and sabotage. The insights gathered from his first envoy to Europe led FDR to dispatch another one the following year to assess strategic options for American military campaigns in the Middle East.
The result of information gathering by these special envoys came in June 1941 with the Creation of an Office of the Coordinator of Information (COI) led by Colonel William J. Donovan. Donovan was an internationally-renowned and highly-decorated WWI hero who had been on both trips and had written a “Memorandum of Establishment of Service of Strategic Information”. FDR charged him with building the clandestine operations group to report directly to the President.
Harpers Magazine a couple months later in August, a little over a year after the fall of France, wrote publicly about Nazi military intelligence using radio broadcasts to undermine resistance. 4
“…announcers would tell their listeners daily: Your leaders are corrupt. Your British Allies are cowards and traitors. The Fuhrer has said time and again: ‘Germany wants nothing of France.’ French listeners! Force your government to make peace!’ Together with such appeals went terrifying proofs of the omniscience of the German Intelligence. On one occasion two French generals sitting down to dinner in the Maginot Line heard on the radio an exact description of the menu.
During this time the “America First” campaigners had pushed a similar line of “make peace” to spread Hitler’s power (and they still continued even through WWII despite sedition charges and conviction of members of “America First”). 5 Because the State Department, Army, Navy and FBI were collecting information in a decentralized fashion, FDR found they didn’t address his need to protect America from the “Firsters”.
When Japan bombed Pearl Harbor months later and Germany declared war on America a dramatic elevation of task was imminent for the COI. The Joint Chiefs of Staff (JCS) began calling for measures of “subversive activity” to undermine German resistance. FDR’s concept of COI was set on a course to answer this call with a specific duty in operations. by the summer of 1942, a year after it was first setup with several hundred civilians reporting directly to the President, COI moved under JCS and was rebranded the famous Office of Strategic Services (OSS).
The JCS issued an OSS mission statement, which echoed FDR’s earlier emphasis: prepare studies and research, plan and execute subversive activity, and operate and train an organization to collect information via espionage. 6
The OSS was formalized into a military outfit because an acute need was perceived by Donovan for strategic analysis of vast information collections. Any initial propaganda functions of the COI were removed, per FDR’s requirement those capabilities not fall under military leadership, handed instead to an Office of War Information. The OSS now sought ways to operate along with other long-established Allied services such as British Military Intelligence, as well as Churchill’s newly formed Special Operations Executive (SOE), in recommending and executing methods to prepare for invasions and lower resistance to military campaigns.
FDR by this time seemingly had built almost a decade of political groundwork for American foriegn intelligence operations. Donovan’s leadership brought to the table a stellar reputation. Despite these huge advantages, the initial steps for OSS as a military service provider were far from easy. Detractors soon demanded trust come from evidence of extensive field expertise and experience with clandestine services, which few Americans could have possessed at its start.
A high bar for staff within the OSS maybe was a reflection of British reputation at the time, given its many decades of running global spy networks and sabotage operations (even a modern cryptanalysis unit “Room 40” — foundation of today’s GCHQ — was created by Winston Churchill in 1914). Orde Wingate, for example, in the late 1930s only was ranked as a junior intelligence officer as he pioneered “Commando” tactics to undermine Arab resistance to British rule.
The British also tended to exhibit overconfidence and unfairly dismiss other services. Collaborations with other nations fumbled so badly, for example, that during a September 1939 invasion by Nazi Germany the codebreakers in Poland already were fleeing for their lives by the time details of breaking German Enigma would be taken seriously by the British. 7 In many ways these failures had laid the groundwork for an American brand of centralized intelligence service to emphasize extremely rapid study and more open collaboration.
At the very least, without having yet built an espionage organization or a methodology for collaboration, OSS initially was built by Donovan as the coordinated path for longer-standing foreign intelligence services to funnel into American military objectives. Arguably this sharing emphasis was a wise move at the time to rapidly train and expand his staff. After WWII a highly-collaborative style confronted Donovan with an image problem, however. Some questioned in public whether the British training the OSS meant it was theirs to drive, and not something uniquely American.
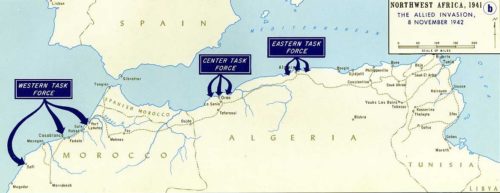
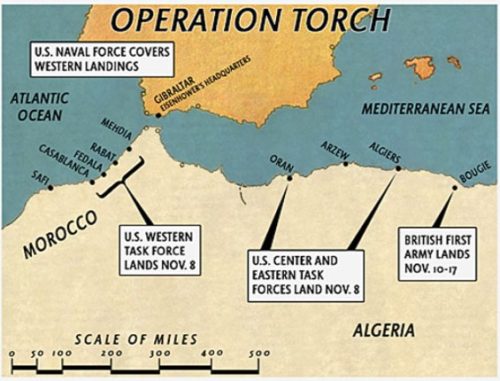
In fact, Donovan quickly proved not only a uniquely American capability of the OSS, he also proved it to be an independent intelligence service provider very useful for military leadership. The first real opportunity to show what OSS could do in active war efforts was Operation Torch of 1942; Churchill and FDR had agreed in July of that year to a joint invasion of French North Africa controlled by the Vichy regime.
The U.S. Fifth Army called the OSS to aid with a November invasion plan in areas of Morocco, while the British called in their SOE for an Algerian front. Analysis scholars of the OSS under Bill Langer and Sherman Kent 8 set about marshaling publicly available data on transit (ports and railway) of North Africa, formulating advice and meaningful action plans (e.g. Algiers became highly targeted for its port, railroad terminal, supply base area and two airfields not to mention seat of government for all French North Africa).
Torch symbolized more than just the test of OSS. It was the first American-led entry into the European war, and was described by General Eisenhower as a test of the Allies bringing “an unprovoked attack upon a neutral country.” 9 Psychological methods were a major consideration as the U.S. military wanted to ensure positive morale for landing forces, as well as lowered resistance from occupied areas, not to mention keeping political support at home.
Here’s an example propaganda leaflet that was titled “Cleaning in Africa” and dropped by the British during Operation Compass (Desert War) in Libya after 1940 (click to enlarge):



The small invasion force of 10,000 troops was believed to depend heavily on a welcome response by the French, while also maintaining secrecy to prevent Axis forces being allocated into the region. These essentially sat in opposition to each other, since secrecy hampered the ability to precisely time local support. General Eisenhower, along with military chiefs, decided the complexity of this would be dealt with best by their newly established OSS using its independent capabilities for sabotage and information warfare.
Success of the OSS during Torch is debated by historians and beyond the scope of this article. Suffice it to say that being overly optimistic meant the U.S. military was faced with significant casualties; resistance falsely was predicted to be minimal (it was fierce) and subversion was ineffective (secrecy made landing coordination improbable). Even the goal of avoiding any build-up of Axis forces did not happen, if we consider mission scope to include the coming Tunisian campaign.
Instead of OSS successes, it was Hitler’s sudden violation of the armistice from 1940 — invading unoccupied parts of France — that brought unexpected relief on American forces. A Vichy authority in Algeria opened the door to negotiation with Eisenhower, signing a cease-fire that stopped resistance and Allied casualty counts.
This cease-fire was the most expedient path to set in motion transition to much larger landing forces, although it risked the Allies dealing with a known Nazi collaborator. French Admiral Darlan signed with American leaders only for a guarantee he would preserve authority over his concept of a French North Africa, as his trust in the erratic Hitler evaporated.
The OSS service, despite these non-optimal results in Torch, became seen by U.S. military commanders as an essential ingredient to future campaigns. A reputation spread for the service being a quick study of foreign data and providing useful analysis. This not only was recognized by Americans, it also led to British clandestine operations increasing in wake of Torch, represented in territorial competitions that would soon emerge. Just three years after Torch some asked whether FDR’s vision and Donovan’s execution had led America to surpass British capabilities in special operations and gathering secret intelligence. 10
After the war ended in 1945 the military operation of OSS led out of “room 109” was shut-down by then president Truman and restarted shortly afterwards without Donovan, renamed as the Central Intelligence Group (CIG). Two years later the CIA was named. 11
Three lessons can be learned from this sequence of events that ended in the creation of the CIA.
First, America before the 1930s was in grave danger as it lacked any mechanism to respond in-kind to active information warfare measures taken by foreign adversaries to undermine a political system. A rush to correct this disadvantage was felt by the U.S. presidential election winner of 1932, given no capabilities on par with German military intelligence methods that had been generating Nazi sympathizers. Moving early and quickly was essential to having later success in information warfare.
Second, America in the 1940s benefited from establishing its own brand of professional spy service (information collection and analysis group) to support its military campaigns heading into neutral third-party states. Their mission was to reduce resistance, minimize casualties, and maintain domestic support.
Third, the expansive global role the U.S. was holding after WWII meant it felt pressure to further expand and maintain its centralized collection of data, and to use propaganda to continue warding off apathy in the face of veiled yet serious threats to democracy.12 Such mass collection of data for analysis continues as the foundation of intelligence programs to this day. Superiority in conflict was achieved by knowing everything possible about an adversary, as a gateway to influencing their decisions and armed political outcomes.
Donovan perhaps said it best when in 1945 he advocated for creating the CIA because “America cannot afford to resume its prewar [America First] indifference…the greatest nation in the world cannot rely upon physical strength alone”. 13
- https://www.theatlantic.com/politics/archive/2016/05/william-randolph-hearst-gave-america-first-itsnationalist-edge/481497/
- David Welch, The Third Reich: Politics and Propaganda, (New York: Routledge, 1994): 38
- https://www.nps.gov/articles/wild-bill-donovan-and-the-origins-of-the-oss.htm
- https://harpers.org/archive/1941/08/u-s-international-broadcasting/
- http://www.ajcarchives.org/AJC_DATA/Files/1944_1945_5_USCivicPolitical.pdf
- Thomas F. Troy, Donovan and the CIA (Frederick, MD: University Publications of America, 1981), Appendix F, JCS 67: 429.
- https://www.commentarymagazine.com/articles/the-man-who-invented-the-commandoswingate-ofpalestine/
- https://web.archive.org/web/20201016184006/https://www.cia.gov/news-information/featured-story-archive/2010-featured-story-archive/sherman-kent-the-father-of-intelligence.html
- Dwight D. Eisenhower, Crusade in Europe (New York: Doubleday, 1948): 86.
- Bickham Sweet-Escott, Baker Street Irregular (London: Methuen & Co, 1965): 126.
- https://www.stripes.com/news/us/birthplace-of-cia-american-spycraft-make-national-register-of-historic-places-1.451217
- Alfred H. Paddock Jr, US Army Special Warfare: Its Origins. Psychological and Unconventional Warfare, 1941-1952 (National Defense University Press 1982): 227
- “Donovan: Father of US Intelligence”, CIA YouTube Video, 26 Jul 2012.
Related Videos
(Deleted by CIA)