
Equifax soaks up a lot of news as the example of bad leadership, and there has been a lot said about the CSO role and person. But is it really the example we should focus on the most?
By the numbers, Equifax appears to sit among a wide group of breaches that each lost around 100-150 million accounts:
- Under Armor
- eBay
- Target
- Heartland
- Rambler
- TJX
- AOL
- MyHeritage
This group is defined purely by a quantitative measure of the 100-150 million accounts breached. It is unclear how adding qualitative measures (e.g. type of data breached) would change these groups much.
Applying qualitative measures doesn’t explain, for example, why breaches of the most sensitive data will still see a responsible CSO treated incredibly lightly. In fact, the larger breaches arguably align with the more sensitive data when you dig into it. Why are these bigger and more severe breaches ignored, compared to the far smaller breach of Equifax? It doesn’t add up.
Instead, when you look for a correlation of CSO to massive breaches (both in terms of quantity and quality of data lost), all three of the following breaches track back to a single person. This person never did the CSO job before (or even did a similar job at a public or large organization), and is alleged to have facilitated atrocity crimes, and I think it fair to say he never should be allowed to attempt it again:
- Yahoo 2013 (undisclosed until 2016) 3 billion breached
- Yahoo 2014 (also undisclosed until 2016) 500 million breached
- Facebook 2017-2019 over 600 million breached
Equifax doesn’t even appear in the “Information is Beautiful” visualization tool that illustrates the world’s biggest “poor security” failures. Facebook is unmistakably largest:
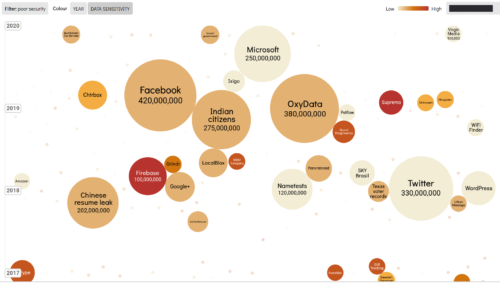
And yet nothing like the following news cycles seems to exist for such an inexperienced, disgraced CSO that was responsible at Yahoo AND Facebook…
- Equifax’s security chief had some big problems…
- Equifax hired a music major as chief security officer…
- Equifax Deep Dive and CSO Qualifications
We need to seriously consider whether an Equifax CSO was treated by social media pundits as an outlier and pilloried because she is a woman held to higher ethical standard than men:
[In a study of sexism at work] …average recommended sentence was around 80 days for Jack and around 130 days for Jane. So that was a difference of nearly two months of jail sentence. …females had a 106 percent higher likelihood of being disbarred than males… punished more severely for the same offenses as men.
Why wasn’t the Yahoo/Facebook CSO scrutinized in a similar fashion given his documented/obvious lack of qualifications in organizational leadership, let alone all the other CSO within the “100-150 million tier” of breached companies?
This question remains open. And why did the Equifax CSO “retire” yet the Yahoo/Facebook CSO get shifted upward to a research position for the very thing he spectacularly failed at?
On top of the massive confidentiality breaches under the Facebook CSO, his legacy also is some of the biggest data integrity failures in history (given 50 million accounts breached, failed to block unfiltered harmful content and is alleged to have facilitated political destabilization and atrocity crimes).
The bottom line is one person attempted to be CSO twice, with no prior experience, and seems to have a track record now of nearly 4 billion accounts compromised with highly questionable disclosure practices. Yet this man seems to have escaped all the scrutiny applied to a woman.
Update Feb 3, 2020:
Vice reports “penalties for data breaches and lax security are often too pathetic to drive meaningful change”.
Update Feb 10, 2020:
While Facebook pivoted its CSO role to an external academic appointment at Stanford, and thus continues to be embroiled in breaches, Equifax went the other direction and has stayed above board.
Statement from the new Equifax CSO, announcing criminal charges, shows a clear resolution, far above the lingering dumpster fire legacy of CSO at Facebook and Yahoo:
This morning, the DOJ identified the perpetrators who attacked Equifax in 2017. With breaches, identification of the attackers (or “attribution”) can be incredibly difficult—even impossible. Being able to share this information is the result of an enormous amount of work by authorities. We cannot thank the U.S. Department of Justice, Federal Bureau of Investigation (FBI), and so many others enough for their tireless efforts to achieve this result.
In parallel, Equifax has been transforming our security program—embedding security into our DNA by driving cultural change, implementing advanced controls tailored to the specific threats we face, achieving relevant certifications, and—just as importantly—sharing what we’ve learned with our customers, partners, and authorities.
Equifax partnered with authorities right from the beginning, and two-way information sharing remains a key part of our security program. The importance of partnering with authorities cannot be overstated. If your security team doesn’t know who to contact at the FBI and the Secret Service, change that today.
At Equifax, we are doing our best to make sure that this never happens again and to support others who want to learn from our experience.
Again, nothing even close to that for Facebook has appeared, only more breaches. Yet the person who said he would lead security has not been held to account for doing the opposite.
Update April 28, 2020:
Insiders at Facebook over the past few years have revealed to me that staff asked to be reassigned away from reporting directly to the CSO, as he lacked basic leadership skill and experience. By the time he was forced to resign he had nobody left under his remit.
This has now been exposed publicly as his legacy not only is the largest breaches in history, but also discredited methods and a group “dissolved and dispersed“.
“Facebook has dissolved and dispersed its security group over the last two years, the people said. The latest cuts are part of a change in philosophy on security efforts, spurred by infighting and long-running issues within the department, they said.”
It boggles the mind how Equifax CSO was getting so much attention instead of this one, a global catastrophe of far greater impact both quantitatively and qualitatively.
As a layman I would guess that since the actual value of the data in the other breeches isn’t as clear, especially to the media, the Equifax breech seemed especially egregious.
Hi Dave, yes I touch on this with the brief note about quality versus quantity of data.
Equifax was 150 million “names, addresses, dates of birth, Social Security numbers, and drivers’ licenses numbers”. That’s not far from the data found in other breaches of the same quantity. It does seem more on the nose than just any random breach given that Equifax, like Facebook, presented itself as a trusted repository of identity data.
That being said the Facebook CSO claimed to work on the most sensitive data with the most capable teams, yet also ran a narrative about being just some basic data and an impossible working environment. Can’t have it both ways. If you’re boasting to the press about being the big officer of security at the most advanced company in the world, yet introduce yourself after breaches as a feckless caged canary taking huge payments to do nothing, what are you even doing in the job?
Meanwhile, Yahoo and Facebook represent over 4,000 million (4b) accounts of nearly everything about someone, far more than name, address, ID numbers and date of birth.
Seems crucial to note while the Equifax data leak never appeared on the resale market, there’s a high likelihood that attackers were Russian or Chinese seeking to ex-filtrate American citizen data (similar to how the “America First” network was a conduit for 1930s Nazi Germany military intelligence). Since people often use Yahoo and Facebook to share far more than their basic ID information. threat actors would find it even more useful in terms of quality than Equifax.