I recently discussed the controversial security firm known as Wiz in one of my previous articles. In that post, I just mentioned briefly a dispute between Wiz and another security company named Orca, which has now brought to light an intriguing revelation about Wiz’s security product.
In a well-documented lawsuit, Orca alleges that Wiz unlawfully appropriated their concepts across various domains, spanning from patents to marketing strategies. To provide some context, the complaint begins with an incident in which the founder of Orca had a meeting with the Microsoft Cloud Security team to present his innovative ideas. Subsequently, members of the Microsoft Cloud Security team departed from Microsoft and established a competing company that directly utilized these very ideas, thus competing with Orca.
Now, at first glance, this may seem audacious and apparent, but it’s essential to understand the context. We’re talking about a closely-knit group of former military intelligence personnel from Israel who have quickly earned a reputation in the civilian market for employing very aggressive and unfair competitive tactics more akin to wartime espionage.
Speaking of espionage, the Orca complaint recently was amended with some proof that Wiz seems to be sneaking data from customers with what seems to be an intentionally unsafe snapshot scanning architecture.
One common practice in cloud management is taking snapshots of customer workloads to create backups or facilitate disaster recovery. And the critical importance of keeping cloud snapshots private is hard to overstate. A supposed security vendor should never roll up to take snapshots of your workloads and read them out somewhere else, especially when claiming to care about your privacy.
But I’m getting ahead of myself.
A cloud snapshot is essentially a very fast point-in-time copy of a virtual machine (VM), it captures an entire workload’s state. It has the data, as well as configuration, and storage at a specific moment. Typically this allows a workload to be restored to that exact state, revolutionizing both backups and restores. Snapshots quickly became indispensable for many uses including tests, migrations as well as aiding business continuity, disaster recovery and reduced downtime.
The snapshots, like the name implies, can contain all kinds of sensitive information, including proprietary data, intellectual property, or customer records. Exposing snapshots to third-party vendors brings to mind huge risks of unauthorized access or data breaches. Given how many industries and regions have strict regulations governing data privacy and security, the very idea of transferring snapshots to external vendors probably trips compliance violations and legal consequences.
FTC are you listening?
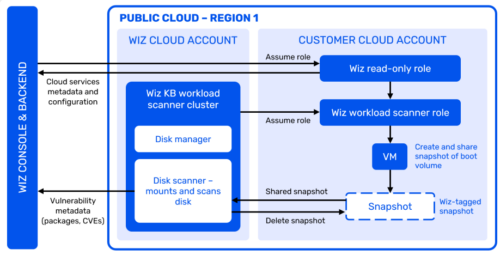
So why would Wiz even think of moving snapshots into their cloud account? Terrible idea and totally unnecessary, a violation of basic safety. Yet here it is, as captured on page 46 in the new Orca amended complaint of September 15th.
Scan configuration — The list of disks for scanning is composed by the cloud fetcher leveraging the cloud provider APIs and sent to the Wiz workload scanner. Snapshot creation — The workload scanner, which runs in a dedicated account, creates the snapshot and shares it with the scanner cluster. These snapshots are created with ‘wiz:auto-gen-snapshot’ tag to help identify them. Snapshot scan — The snapshot is mapped as a read-only volume and scanned. The scan results include metadata on packages, vulnerabilities and mis-configurations and are sent to the backend. Cleanup — The snapshot is deleted from the customer tenant.
Orca’s complaint calls out a marketing detail here. Apparently they pitched and grew their technology using the concept of their scanner looking at cloud machines like an MRI scans the human body.
Orca realized early on that its cloud-native approach could be analogized to a medical MRI, providing a full model of the cloud environment without affecting it in any way. Early Orca marketing materials noted: “An apt analogy is to think of a medical MRI. Instead of probing inside the body with needles and scalpels, such imaging is an out-of-band method of obtaining a detailed picture of the organs and tissue within. The person is never physically touched.”
Page 10 of the complaint says Wiz then copied this MRI language from Orca almost word-for-word into their own marketing.
Just like an MRI performs a 3D scan of the body without affecting the body itself, snapshot scanning achieves deep analysis of the workload without any impact or interruption to the live workload
The problem, beyond stealing the marketing, seems to be that Wiz documentation also says snapshots are “always remaining within the customer tenant” yet their architecture illustrates that is NOT true: a “shared snapshot” is read into the Wiz cloud account and outside customer control.
That’s not “always remaining within” if you believe Wiz themselves when they jump up and down and scream at Microsoft for having a private key configured to be read by someone other than the person who owns that key. No joke, Wiz couldn’t be more excited to tell the world that Microsoft was “breached” yet here in their own documentation they seem to have designed a safety breach as inherent to their product architecture.
For comparison, Orca documentation has a very important statement that says basically the exact opposite to Wiz.
Note that these snapshots can only be accessed from your account for security.
Again, looking at the Wiz documentation in the complaint, it seems like Wiz created a snapshot flow that setup access from outside the customer account. How could they be so upset with Microsoft, their former employer, for excessive permissions in cloud when they just build an entirely new cloud scan empire based on excessive permissions?
Security vendors, no matter how reputable (no matter if they call themselves the untouchable “Wiz”ards), are not inherently safe and of course may themselves become targets. Their handling of snapshots increases attack surface and exposure to potential breaches.
Also data is subject to the laws and regulations of the country or region where it is located. Wiz shifting snapshots could mean they “somehow” show up in Israel with its different rules, creating compliance challenges.
What do I mean, could mean?
Read the Orca complaint in full, which documents how Wiz allegedly built their company from a culture of cynical extrajudicial military-espionage that goes even beyond industrial theft.
And then ask yourself why their architecture allegedly was built for stealing customer data in snapshots…
 I know it’s fashionable to say cloud security means an ever-changing landscape, but in reality our book “Securing the Virtual Environment: How to Defend the Enterprise From Attack” from ten years ago still lays out principles that remain steadfast cornerstones. Safeguarding customer workloads and data is a top priority, such that it is unequivocally recommended to refrain from shifting snapshots to third-party security vendors. Keep them private, under strict access control so you can monitor activities, and ensure compliance with regulations, laws and security policies.
I know it’s fashionable to say cloud security means an ever-changing landscape, but in reality our book “Securing the Virtual Environment: How to Defend the Enterprise From Attack” from ten years ago still lays out principles that remain steadfast cornerstones. Safeguarding customer workloads and data is a top priority, such that it is unequivocally recommended to refrain from shifting snapshots to third-party security vendors. Keep them private, under strict access control so you can monitor activities, and ensure compliance with regulations, laws and security policies.
- July 2023: Orca-vs-Wiz-Lawsuit-Complaint
- September 2023: Orca-vs-Wiz-Amended-Complaint
- September 2023: Orca-vs-Wiz-Amended-Complaint-Exhibits_2023-09-15
My personal favorite line:
Security vendors, no matter how reputable (no matter if they call themselves the untouchable “Wiz”ards), are not inherently safe and of course may themselves become targets. Their handling of snapshots increases attack surface and exposure to potential breaches. Also data is subject to the laws and regulations of the country or region where it is located.
Behold, I have traversed the vast realms of the digital expanse and stumbled upon thy blog post, a beacon of wisdom. In the spirit of Gandalf, I commend thee for thy insights on data privacy—a topic as precious as the One Ring. May thy words echo through the digital corridors, enlightening minds and fostering a fellowship dedicated to safeguarding the sanctity of personal information in this age of virtual wizardry. Well done, my digital companion!