Recently I wrote about developments in airborne information warfare machines.
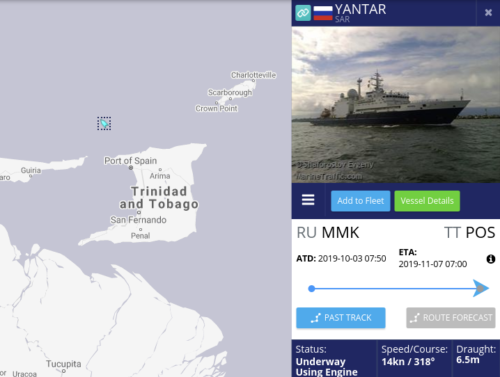
Also in the news lately is an infamous Russian “seabed warfare” ship that suddenly appeared in Caribbean waters.

She can deploy deep-diving submarines and has two different remote-operated vehicle (ROV) systems. And they can reach almost any undersea cable on the planet, even in deep water where conventional wisdom says that a cable should be safe.
In the same news story, the author speculates that ship is engaged right now in undersea cable attacks.
…search patterns are different from when she is near Internet cables. So we can infer that she us doing something different, and using different systems.
So has she been searching for something on this trip? The journey from her base in the Arctic to the Caribbean is approximately 5,800 miles. With her cruising speed of 14.5 knots it should have taken her about two weeks. Instead it has taken her over a month. So it does appear likely.
The MarineTraffic map shows the ship near the coast of Trinidad.
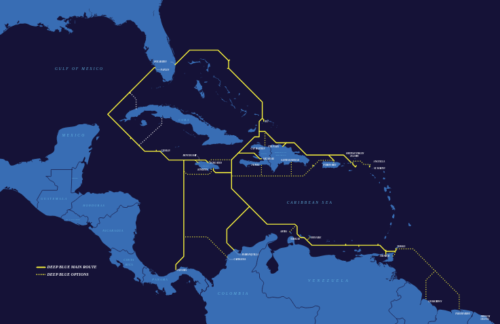
Maps of the Caribbean waters illustrate the relevance of any ship’s position to Internet cables and seabed warfare.
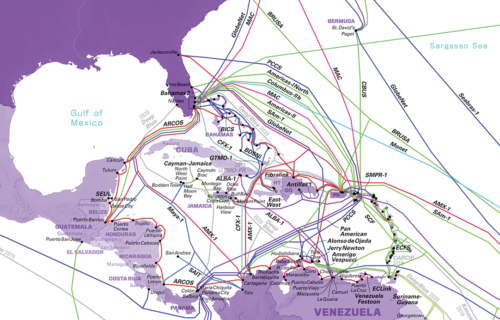
A Russian ship on the northwest coast of Trinidad means it’s either inspecting or even tapping into the new DeepBlue cable, listed as going online 2020. Trinidad is in the lower right corner of the above map. Here’s a zoomed in look at the area to compare with the ship position map above:
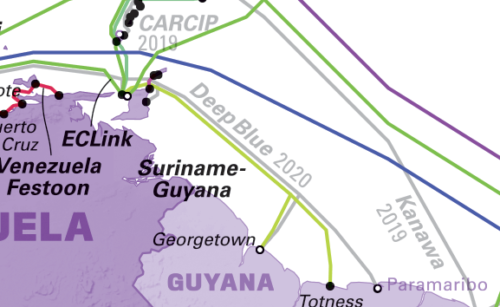
And the DeepBlue cable specs give a pretty good idea of why a Russian seabed warfare ship would be hovering about in those specific waters…
Spanning approximately 12,000 km and initially landing in 14 markets, the Deep Blue Cable will meet an urgent demand for advanced telecom services across the Caribbean. This resilient state-of-the-art cable has up to 8 fibre pairs with an initial capacity of 6Tbps and ultimate capacity of approximately 20Tbps per fibre pair. It is designed to be fully looped maximizing system resiliency. With more than 40 planned landings, Deep Blue Cable will bring 28 island nations closer to each other and better connected to the world.
In only somewhat related news, the U.S. has been funding a scientific mission with the latest undersea discovery robots to find missing WWII submarines.
The USS Grayback was discovered more than 1,400 feet under water about 50 miles south of Okinawa, Japan, in June by Tim Taylor and his “Lost 52 Project” team, which announced the finding Sunday.

Their announcements are public and thus show how clearly technology today can map the seabed.
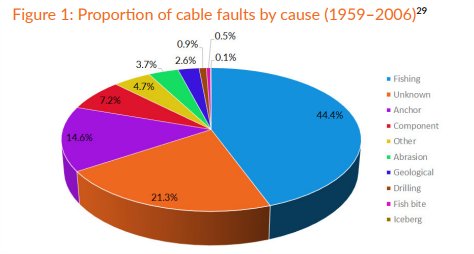
It is a far cry from the Cold War methods, as illustrated in this chart of cable faults since 1959 by cause (in a report from UK think tank Policy Exchange):
The 21% fishing breaks really should have been split out more, given how the same Policy Exchange report reveals Russia “accidentally” cut cables via unmarked fishing trawlers that would hover about.

To put it another way, while nobody could positively catch these fishing boats cutting transatlantic cables, the book “Incidents at Sea” explains how breaks jumped 4X whenever the Russians would drag tackle anywhere near a cable.

In just four days of February 1959, a series of twelve breaks in five American cables happened off the coast of Newfoundland, with only the Russian Novorossiysk trawler nearby.
As the caption of the above historic press photo explains, the US Navy (USS Roy O Hale) intercepted the trawler boarded her and searched for evidence of intent to break cables.
While broken cable was found on deck, the crew claimed they found cutting it the best option to free their nets from being tangled.
Nothing conclusive was found either way, so the case remained open as Russia complained about unfair detention of its citizens and the US complained about an 1884 Convention for the Protection of Submarine Telegraph Cables.
Update February 11, 2020: “New Pentagon Map Shows Huge Scale Of Worrisome Russian and Chinese Naval Operations”
Though the map does not say what time period it covers and or what types of naval vessels were necessarily present in specific locations and when, it does confirm that there has been notable Russian naval activity off the coast of the southeastern United States, as well as in the North Atlantic Ocean and Caribbean, in recent years.
This new map confirms much of what has been talked about for years, although it also reveals a high amount of Chinese naval activity off the coast of Mozambique.
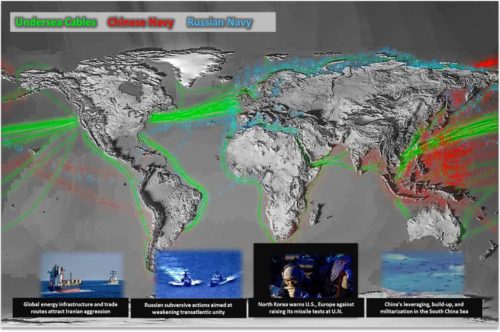
I don’t think I’ve ever seen mention of China’s heavy activity in southern African waters. The opposite, actually, as India and Mozambique recently made very public that they signed an agreement to apply pressure against Chinese ship movements in that region.
Ahead of undertaking a three-day visit to the southern African country of Mozambique, Indian Defence Minister Rajnath Singh on Friday said that the two countries will sign agreements in the fields of “exclusive economic zone surveillance, sharing of white shipping information and hydrography”.
A Chinese government promotional video for their 25th Fleet visiting Madagascar, however, offers the explanation that since “December 2008, authorized by the United Nations, the Chinese navy has been sending task forces to the Gulf of Aden and Somali waters for escort missions” before touring the coastline.
Apparently 2012 was the last time a Chinese fleet (the 10th) was in Mozambique, so that may be a clue to the age of the newly released DoD map.