The Institute for Soldier Nanotechnologies at MIT together with the Defense and Veterans Brain Injury Center has released a study of blasts, helmets and brain injury. They set out to test a theory that military traumatic brain injury is made worse by the current helmet design.
Compared to the unhelmeted head, the head with helmet experienced slight mitigation of intracranial stresses. This suggests that the existing [Advanced Combat Helmet] ACH does not significantly contribute to mitigating blast effects, but does not worsen them either. By contrast, the helmet and face shield combination impeded direct transmission of stress waves to the face, resulting in a delay in the transmission of stresses to the intracranial cavity and lower intracranial stresses. This suggests a possible strategy for mitigating blast waves often associated with military concussion.
They designed and ran computer simulations, which concluded the opposite; a helmet does not make the blast effect worse but could be improved to reduce damage. The simulation found that the brain is exposed to blasts through the front of the skull due to the soft skin and holes (e.g. nose and eye sockets) — areas that offer the least protection. A face shield is therefore proposed.
The study is interesting because of evolving threats. Helmets have been studied for impact on a hard surface or for penetration by a sharp object. The rise in brain injuries led to a question about the suitability of existing helmets for the latest attack conditions.
Blast-induced traumatic brain injury is the most prevalent military injury in Iraq and Afghanistan, yet little is known about the mechanical effects of blasts on the human head, and still less is known about how personal protective equipment affects the brain’s response to blasts.
This study brought to mind Florence Nightingale’s “coxcomb” graph (now called a polar-area diagram). She illustrated her Notes on Matters Affecting the Health, Efficiency and Hospital Administration of the British Army in 1858 with this graphic showing cause of death in the Crimean War. Wounds (small red slices) caused only a small fraction of the overall body count. Diseases (big blue slices) were the biggest threat to life. The black slices denote an “other” category:
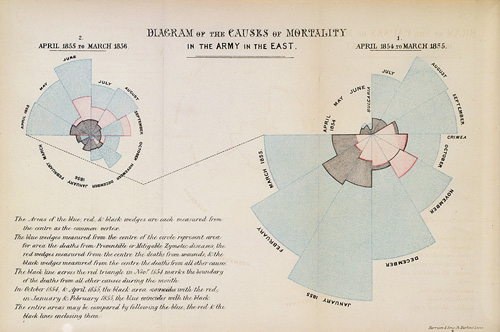
Her chart has been criticized for accuracy as well as style. A bar chart would be more contemporary but, in terms of this blast study on helmets and casualties, I have seen neither.