The nature of propaganda is that a tiny seed of truth is grown into massive distraction.
People tend to overlook the basic fact that an adversary has used a tiny seed to confuse their whole plans. Any sense of real progress — ultimately a target’s fractured resources are more easily divided or disabled from within than confronted as a whole directly from the outside — falls victim to a tactic that really shouldn’t be so easy.
The problem, to paraphrase Mark Twain, is that it’s much easier to manipulate people than to persuade them they’re being manipulated.
I’ve presented about this many times in the past, such as 2012 when I explained how Vanuatu’s rapid mobile phone adoption made it ripe for a political coup by manipulating voters. Most recently I spoke of the Russian government targeting foreign athletes with psychological warfare to “get in their heads” and reduce competitive performance against weaker Russian athletes.
Some new analysis from the alliance for securing democracy shows how this all works. Their “Hamilton Dashboard” highlights two important findings in a post titled “Why the Jeffrey Epstein saga was the Russian government-funded media’s top story of 2019”
…few topics dominated the Russian government-funded media landscape quite like the arrest and subsequent suicide of billionaire financier and serial sex offender Jeffrey Epstein. In its year-end review, RT named the Epstein saga “2019’s major scandal,” and RT UK media personality George Galloway listed it as his number one “truth bomb” of the year (ahead of all the aforementioned events). Given the lack of any notable connection between Epstein and Russian interests, the focus on Epstein highlights the Kremlin’s clear prioritization of content meant to paint a negative image of the West rather than a positive image of Russia.
The first finding is a somewhat obvious one that Russia actively uses seeds that are meant to destroy positive imagery of the West (i.e. reverse the “Hope” campaigns that had resulted in President Obama). Epstein falls into this category.
The second finding is more subtle and implicit. Russia fails miserably to generate any positive image of itself. Every analysis I have read suggests Putin is both desperate and incompetent at forming a national identity, despite ruthlessly positioning himself as a long-term dictator with total control of all resources.
To put it in some context, Putin is a trained assassin, with little to no evidence he can develop a sense of national interest or ability to convey any leadership story about belonging. In fact, these two positions may be contradictory (inherent weakness of being an assassin) given how anyone forming greater identity and purpose would be assassinated; rise of identity could be seen as potential threat to the man with an artificially inflated sense of self worth above everyone else.
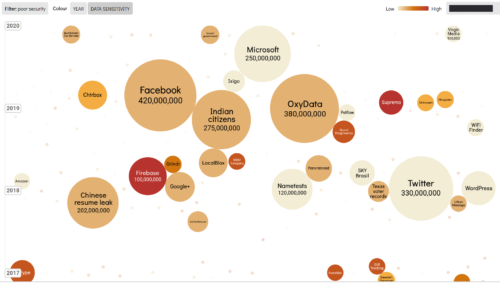
Anyway the graphic for the Hamilton Dashboard of the securing democracy site really caught my eye as a beautifully done rendition of the classic Soviet propaganda art that Putin seems incapable of achieving (a bit like doing the work for him):

For comparison here’s some actual Soviet propaganda that celebrates creating a powerful aviation industry (a suspicious claim given staggering death tolls in their airline: in 1973 alone the Soviet aviation industry had 27 incidents and 780 people were killed)

This genre of “positive” spin poster of prosperity was backed by a complete suppression of any and all “unfavorable” communication that would challenge a progressive narrative (e.g. propaganda seeds of despair pushed by running a story about Epstein). Especially suppressed by the Russians were news of crimes against humanity (massacres, famines and energy/environmental disasters on Russian soil).
In other words, two diametrically opposed threads can be tracked in Cold War propaganda, posters of hope by the Soviets and counter-posters of despair by the CIA (the subject of Putin’s study while in the KGB).
Example of a Soviet poster pushing a positive narrative of prosperity from labor:

Contrarian example of a CIA poster pushing negative narratives (indirectly via Italian media platforms) of demoralizing labor brutality:

In the modern context, being the typical self-promoting KGB agent trained in the art of copying everything the CIA did and trying to use it for his own gain, we see clear evidence in the Hamilton Dashboard that Putin is pushing a despair campaign using today’s social media platforms. He doesn’t, however, seem to be able to come up with any positive sense of identity for his own nation.
And I have to say, despite me being a student of these communication methods (even having a degree related to their usage) my attempts at art in this domain simply pale in comparison to what the Hamilton Dashboard has come up with.
Hats off to them…although really I would expect some despair in their graphic if they wanted to play this game right. I mean it seems a bit counter productive to gift the enemy with banner-level positive glorification imagery that everyone sees when they come to study the enemy.
The same mistake probably should be said for me, in retrospect, as here’s my 2017 image that used to show up in many of my presentations:

It was a refresh of the 2016 rendition that was even more snarky about the U.S. being way ahead in kinetic yet woefully behind in the more pressing cyber domain…